Secure Shell, or SSH in short, is a remote connection protocol in Linux as well as other operating systems. It was first introduced as a replacement for telnet, which did not encrypt password information over the remote connection, and hence can be vulnerable to even simplest of attacks. SSH on the other hand uses advanced cryptography techniques to establish connection (Eg. RSA).
Open SSH is a free and open source implementation of SSH protocol in Linux.
Installing ssh and sshd
On Ubuntu and Debian, the package ssh can be used to install both Open SSH client and Open SSH server.
sudo apt install sshOn CentOS and Fedora, run:
yum install openssh-server openssh-clientsStart SSH daemon to Allow Remote Connections
sshd is the daemon installed with Open SSH packages. To start the daemon, simply run:
sudo service sshd startConnect to Remote Computer
To connect to a remote computer using SSH, an SSH daemon must be installed and running on that computer. You need to know the Hostname or IP Address of the computer and the username and its password. Needless to say, the computer should be accessible from your network.
ssh user@hostname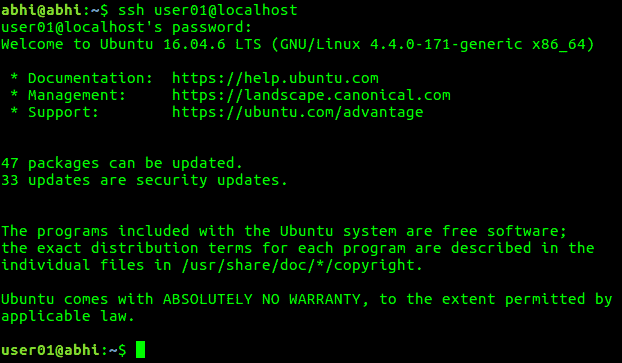
Many a times for automation purposes, there is a need to login to a remote computer without a input prompt for password. To achieve this, we use the RSA authentication method in SSH:
First, generate RSA key for SSH for your user:
ssh-keygen -t rsa
When prompted for a passphrase for this key, you may enter a passphrase as an additional security layer, or leave it empty.
We add this generated key to the authentication agent by running:
ssh-addAim is to copy this generated key to the remote computer. Hence, there has to be one login to the target computer/user to copy this generated key to the remote computer’s SSH config. ssh-copy-id copies the current users’ SSH key to a target computer:
ssh-copy-id username@hostname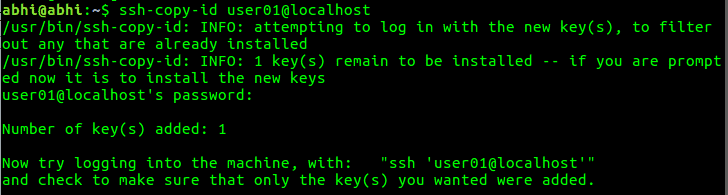
Now you can login without password:
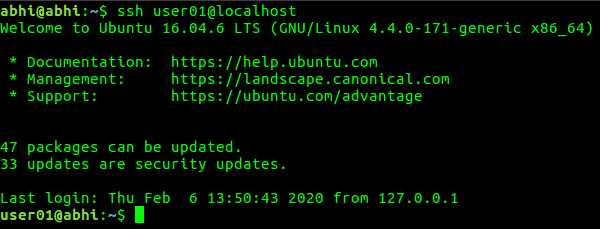
We hope you find the information on this page helpful. If you have any questions, get in touch with us on Twitter.




Member discussion