Linux and Unix based operating systems have been at the core of the fields of Information Security, Network Security, Cryptography, etc. They come with a wide variety of tools meant of cyber security purposes.
Let us take a look at three such tools: Aircrack-ng, Jack The Ripper, and Radare2.
Aircrack-ng Suite
The Aircrack-ng suite is perhaps the most widely used set of WiFi network sniffing and password capturing tools. It is meant to crack IEEE 802.11 protocol wireless network passwords, which are mostly protected by Wifi Protected Access (WPA) or Wifi Protected Access 2 (WPA2) standards and authenticated by Pre-Shared Key (PSK) authentication method.
It offers seperate programs for monitoring status of network devices, capturing packets and dumping in files, cracking passwords, etc.
Note that cracking WPA/WPA2 using crypto-algorithms has been found by researchers to be nearly impossible. Hence, the way to crack WPA/WPA2 by programs like aircrack-ng, is Brute Force and requires a dictionary of passwords to crack it. That means it can only crack the password if the password is a dictionary word.
You can easily Install Aircrack-ng on your system using the installer script provided by packagecloud.io. Open the terminal, and run the following commands based on your Linux OS type.
On Debian based distributions, run the following command:
curl -s https://packagecloud.io/install/repositories/aircrack-ng/release/script.deb.sh | sudo bashFor Red-hat Package Manager (RPM), run the following command:
curl -s https://packagecloud.io/install/repositories/aircrack-ng/release/script.rpm.sh | sudo bashNow let’s try to crack password of a local Wi-Fi network using Aircrack-ng.
Firs of all, run command iwconfig to find the name of your wireless network interface.
iwconfig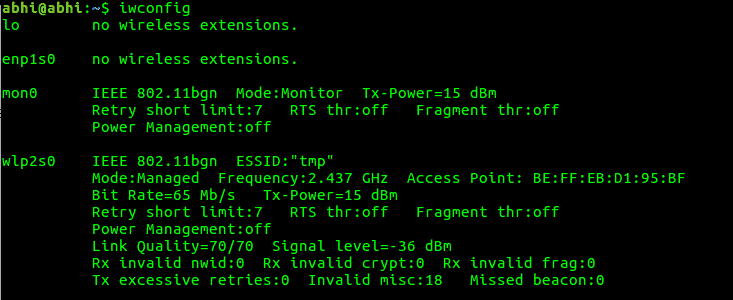
Here, wlp2s0 is the name of my wireless interface. ESSID, i.e., the network name is “tmp”, which is the name of Wifi network I am connected to.
We’ll use the airmon-ng command to start a network monitor interface on wlp2s0.
sudo airmon-ng start wlp2s0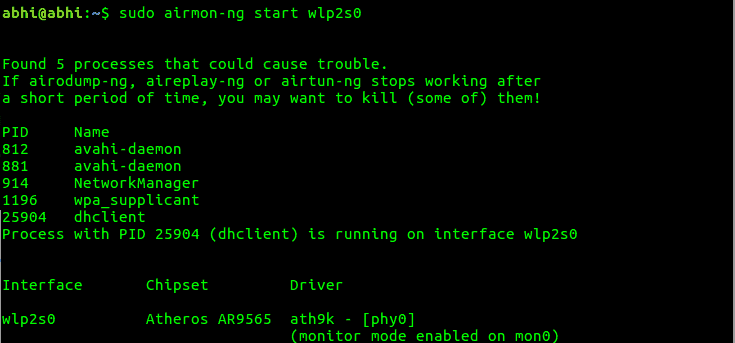
Look for the line at the end to find the monitor mode interface. In the example above, it is mon0. We’ll now start catching network packets by running the airodump-ng on mon0.
sudo airodump-ng mon0 -w logIt displays a monitor of network packets caught from different networks. The -w log part is for saving the network packets in log files. Prefix of the log files will be the part specified after -w, in this case ‘log’.
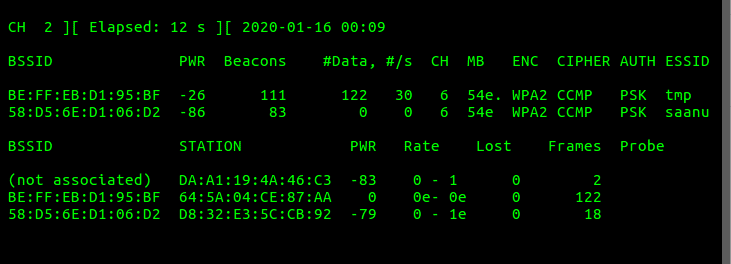
For the program to catch the passphrase hash key, a WPA handshake must take place on the network, i.e., a user should try to connect to it. User can himself disconnect his Wifi, and reconnect to it. On the top right corner now, it notifies that a WPA handshake has been caught.
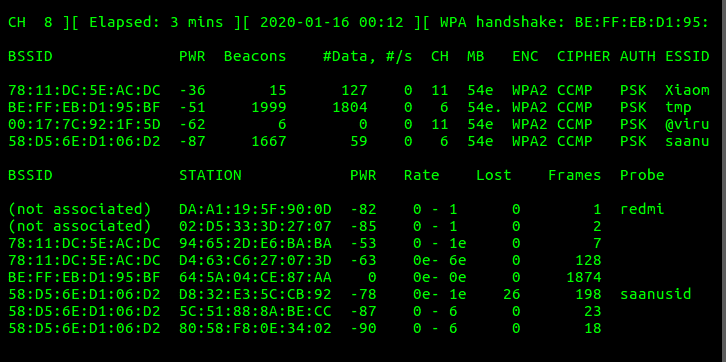
Now, press Ctrl + C to terminate the dump. You can see the generated log files in the current folder.
Next and final step is to run aircrack-ng with a dictionary to see which word matches to the intercepted hash key from the handshake.
aircrack-ng log-01.cap -w tmpdict.txt Here log-01.cap is the logfile generated by airodump-ng command and tmpdict.txt is the dictionary file. Several large dictionaries are available online which can be downloaded and used here.
To select a target network, enter the index number for the network from list of networks shown on the screen.
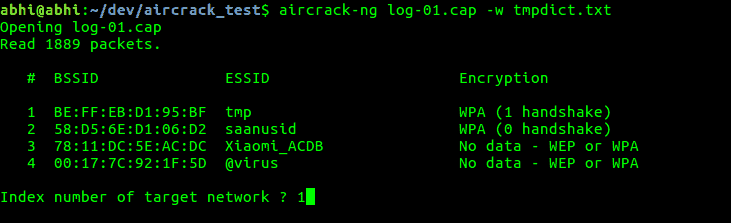
If a key is matched from in dictionary, it will stop and display the following message.
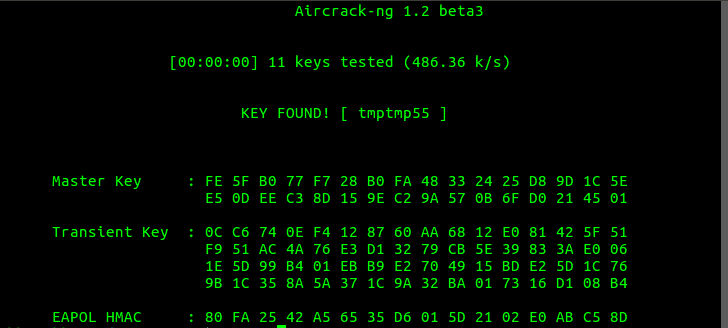
It is obvious that in case of larger dictionary files, the program will take more time to run, as it checks for every entry in the dictionary.
As mentioned before, the password can only be cracked if it is present in the dictionary file. WPA security is strong enough that use of any crypto algorithm will not enable cracking of password. Hence, it is a good practice to have a strong long password with multiple special characters on your Wifi device, so that any kind of password cracking activity never succeeds.
John The Ripper
John the Ripper is a tool used to crack weak Unix passwords. It is a very easy to use tool invoked on password files. It runs in three modes.
Single Mode
Checks all GECOS fields for password, i.e., check for password in user account information; user name, first name, last name, etc.
sudo john --single /etc/shadow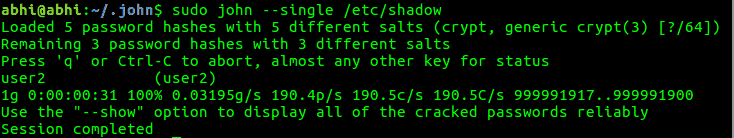
Wordlist Mode
Checks password with each entry from a wordlist (dictionary) file.
sudo john --wordlist=passlist.txt /etc/shadow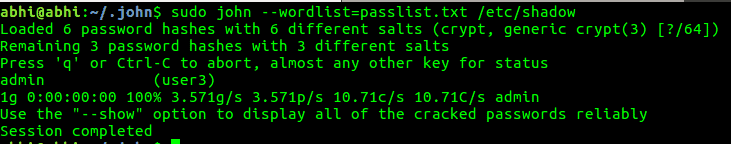
Here, password of user ‘user3’ is “admin”. John was able to crack it because the phrase ‘admin’ was present in passlist.txt file.
Incremental Mode
Check all possible combinations for a configured range. By default it considers all characters in ASCII character set and all lengths from 0 to 13. Needless to say, depending on the configured range, this mode can take huge amount of time to run.
The configuration for this can be changed in /etc/john/john.conf file.
sudo john --incremental /etc/shadowRadare2
Radare2 (alias r2) is a reverse engineering tool for Linux. It can disassemble, debug an executable binary file, with a huge list of options to manipulate data at runtime.
Let us see how to disassemble a very small C program using r2. Note that a basic understanding of assembly language is required to use the tool.
First, create a small C program in either vim or any editor of your choice.
/*test.c*/
#include<stdio.h>
int main() {
int i = 0;
printf("%d\n", i);
return 0;
}As you can see, all this program does is store the digit 0 in a variable, and access the variable to print it.
We shall now compile the program.
gcc test.c -o testAn executable file is created in current directory with name ‘test’. Run it to see output ‘0’.
./test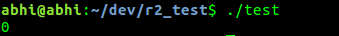
Let’s install r2 now. The package name in Ubuntu and similar distributions is radare2.
sudo apt install radare2Note: For older Ubuntu versions (version 14.04 and below), you need to use apt-get should be used instead of apt.
We will now start the r2 command prompt with our executable file, ‘test’.
r2 test
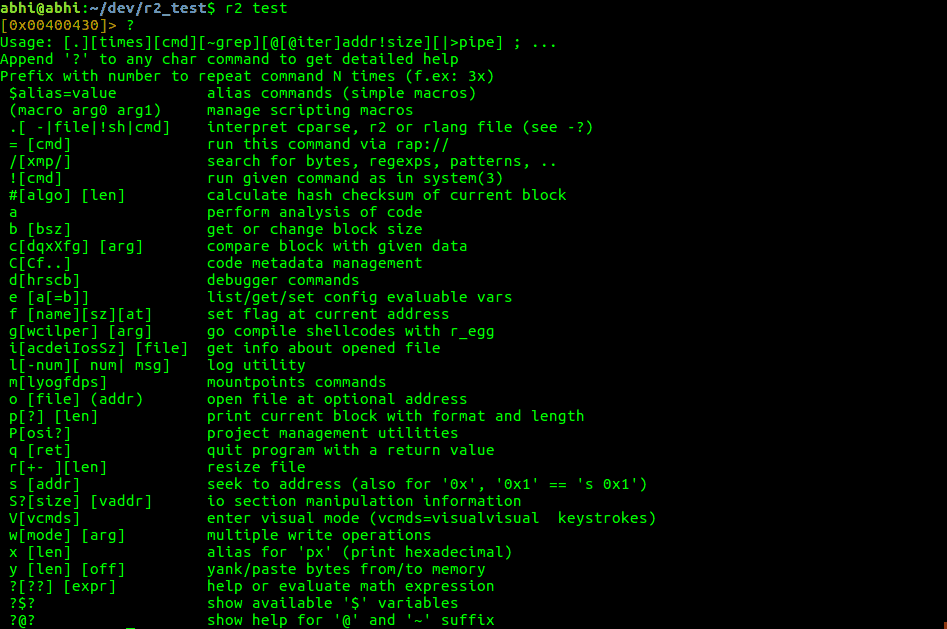
To get list of subcommands, enter <command_name>?. Eg. to get list of subcommands for command a, enter a?
a?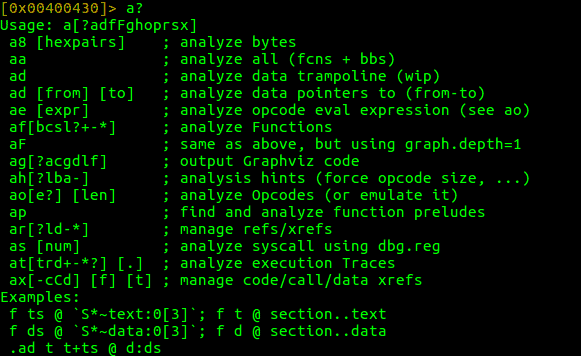
We will run the subcommand aa, which will analyze the complete binary file. It will not output anything. But after analyzing the binary, we can use the p? subcommands to disassemble the code.
Next, we move to the main function of the program. Every executable C program has the main function as its starting point.
s main
You can see that the prefix of prompt has changed the current memory address, i.e., the program is now sought to the address of function main.
Next we use the subcommand pdf, which will print the disassembly of a function. We call it with sym.main, which is the name of main function in assembly language.
pdf sym.main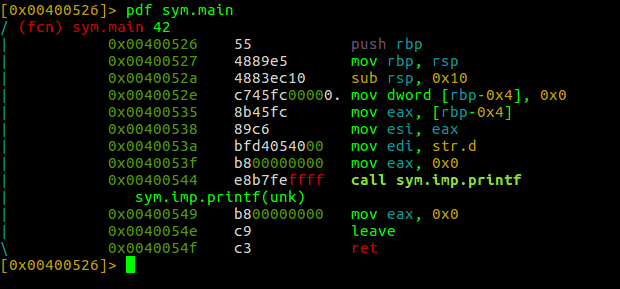
As we can see in the screenshot above, we have the complete disassembly of our C program. We can now analyze what the program is doing by reading the assembly.
For example, mov dword [rbp-0x4], 0x0 is assignment of a value (0) to a memory location rbp – base pointer, 0x4 — Memory size required for an integer.
We have call sym.imp.printf, which will print contents of register eax, i.e. the value 0.
There are many more options for manipulating and debugging the flow of a program in r2. You can try other options which are shown with the ? command. To save any log or disassembly output to a file, you can pipe the output as below:
pdf main > main.sThis was the overview of some of the most widely used hacking tools in Linux. If you found this page helpful, be sure to share it on your favorite online communities.

