Call of Duty: Black Ops 7 launches on November 14, 2025 with stricter anti-cheat on PC. RICOCHET requires both Secure Boot and TPM 2.0 during the beta (Early Access on October 2, Open Beta on October 5) and at launch. If either feature is disabled or unavailable, the game won’t start. At launch, RICOCHET will also introduce remote verification (remote attestation) that validates TPM 2.0 and Secure Boot against Microsoft’s cloud, making local spoofing far harder.
Check your current status in Windows
In under a minute, you can confirm whether you’re already good to go.
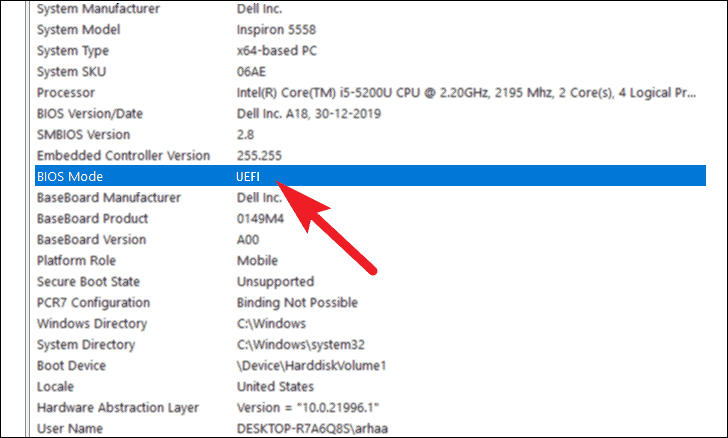
- Press the Windows key, type
msinfoand press Enter. - In System Summary, verify:
- Secure Boot State: On
- BIOS Mode: UEFI
If both lines match, you’re ready for Black Ops 7 on PC. If BIOS Mode shows Legacy and/or Secure Boot State is Off or Unsupported, follow the sections below.
Verify TPM 2.0 is ready
- Press
Windows key+R, typetpm.msc, press Enter. - In the middle pane, confirm Status shows “The TPM is ready for use” and version 2.0.
If TPM isn’t ready or is disabled, enable it in your motherboard firmware (often labeled PTT on Intel, fTPM on AMD). Exact steps vary by vendor; if you need vendor-specific directions or BIOS updates, use the official TPM/Secure Boot help hub for step-by-step guidance and motherboard guides.
Note: TPM 2.0 is a baseline requirement for Windows 11, so systems still on Windows 10 are more likely to find TPM disabled in firmware.
Confirm your system drive uses GPT (not MBR)
- Right-click Start, select Disk Management.
- In the lower pane, right-click the disk that contains your Windows (C:) partition (often “Disk 0”), then choose Properties → Volumes.
- Check Partition style: it should read GUID Partition Table (GPT).
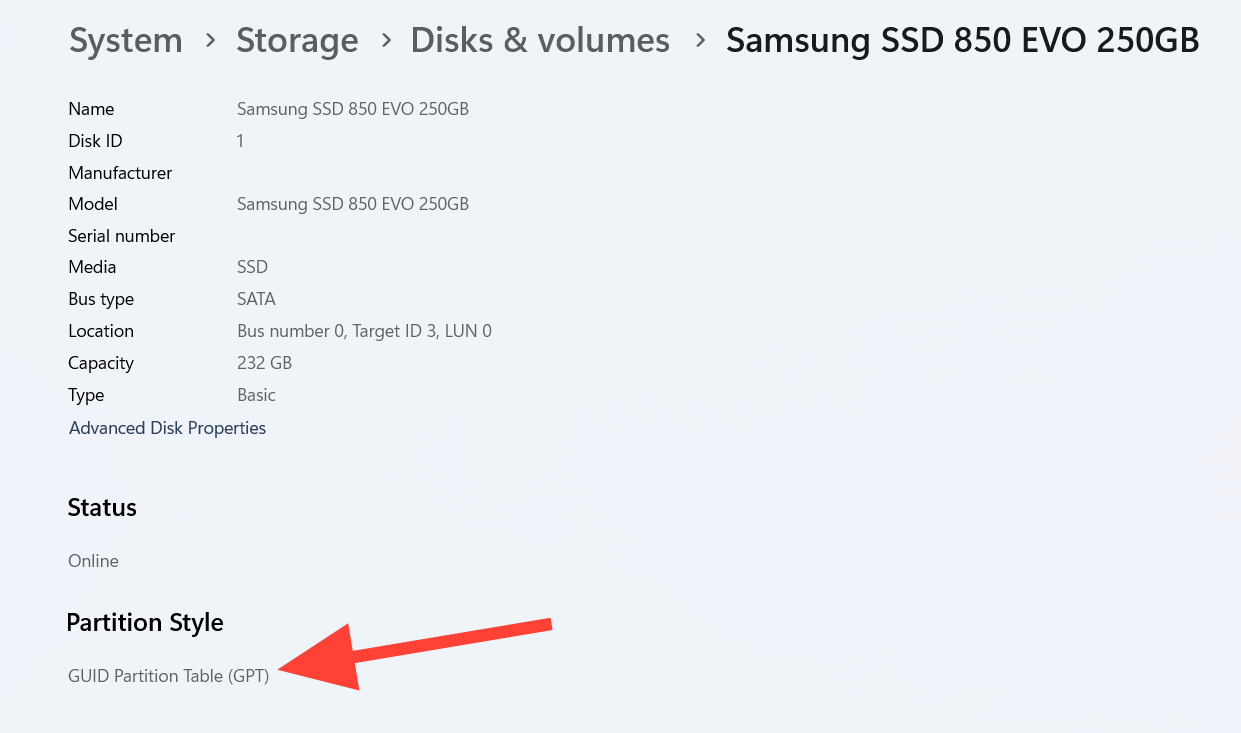
If your boot disk is MBR, convert it to GPT before turning on Secure Boot.
Back up your data first. The built-in tool is designed to be non-destructive, but any partition change has risk.
Run Command Prompt as administrator, then:
mbr2gpt /validate /disk:0 /allowFullOS
mbr2gpt /convert /disk:0 /allowFullOS
Replace 0 with your actual Windows boot disk number if different.If validation or conversion fails, review the message for required actions. Some boards may require switching firmware to UEFI before conversion can complete.
Switch firmware to UEFI and disable CSM
- Restart and enter your motherboard firmware (commonly F11, F12, or Delete at boot).
- Open Advanced settings and locate Boot options.
- Disable CSM (Compatibility Support Module) to enforce pure UEFI mode.
- Save and reboot.
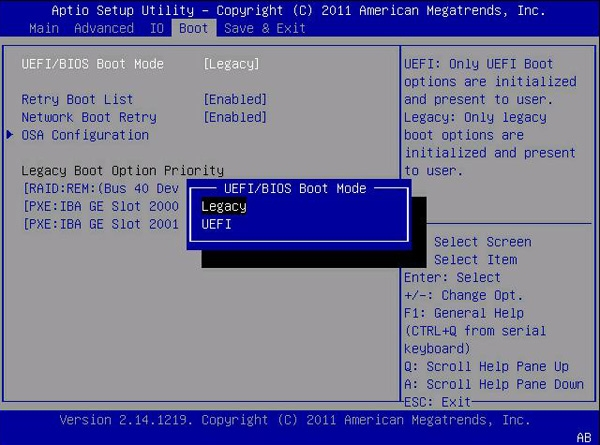
After booting back into Windows, re-run msinfo to confirm BIOS Mode: UEFI.
Enable Secure Boot
- Re-enter your motherboard firmware.
- Open Boot or Secure Boot settings.
- Set Secure Boot to Enabled. Some boards label the mode as Windows UEFI; selecting that applies the correct policy.
- Save changes and restart.
Back in Windows, confirm Secure Boot State: On in msinfo.
What to do based on what you see
| What Windows shows | Next steps |
|---|---|
| UEFI + Secure Boot On | No action needed — you’re ready for Black Ops 7. |
| UEFI + Secure Boot Off | Enable Secure Boot in firmware (Boot/Secure Boot menu → Enabled or Windows UEFI mode). |
| Legacy + Secure Boot Off | Enable TPM 2.0 → Convert system disk to GPT → Disable CSM to switch to UEFI → Enable Secure Boot. |
| Secure Boot State: Unsupported | Check for motherboard BIOS updates. Some boards require newer firmware to support Secure Boot and remote verification. |
| TPM not ready or missing | Enable fTPM/PTT in firmware; if unavailable, update BIOS. Use official TPM/Secure Boot guides for vendor-specific steps. |
Why TPM 2.0 and Secure Boot are mandatory for Black Ops 7
Secure Boot blocks untrusted low-level code from loading at startup and ensures the OS boots in a trusted state. TPM 2.0 provides a hardware-backed root of trust that can store measurements and keys tied to your platform. Together, they harden the PC against pre-boot and early-boot tampering — a common way cheats try to gain the highest possible privileges.
RICOCHET’s next phase adds remote attestation at launch, validating your Secure Boot and TPM configuration against Microsoft’s cloud instead of relying only on local checks. That makes it significantly harder to spoof a compliant system and reduces the window for bypass tools that depend on local manipulation.
What changes during the beta and at launch
- Now through beta: TPM 2.0 and Secure Boot are required to play on PC. RICOCHET systems will be deployed dynamically during the beta to learn normal player behavior and tune detections in real conditions across thousands of hardware setups.
- At launch (Nov 14): Remote attestation comes online alongside upgraded detection systems. RICOCHET’s machine learning models — trained on extensive recent gameplay — focus on differentiating natural aim from aimbots and flagging wallhack-like behavior more quickly on a stronger backend.
The goal isn’t “zero cheaters,” which isn’t realistic, but to raise the cost and complexity of cheating while improving the speed and accuracy of removals.
Troubleshooting
- You use BitLocker: Converting MBR→GPT and changing boot mode can trigger recovery prompts. Have your recovery key handy and complete a full backup before you begin.
- Older motherboards: Some boards require a BIOS update to expose fTPM/PTT or to properly report Secure Boot for remote verification. Check your vendor’s support page if options are missing.
- Drive won’t convert:
mbr2gptwill print reasons for failure (for example, too many partitions). Resolve the listed issues, validate again, then convert.
Set yourself up now
Do the Windows checks, convert to GPT if needed, switch to UEFI, and enable Secure Boot while there’s still time before launch. If your firmware menus don’t match the steps above or you hit a dead end, the official TPM/Secure Boot help hub includes detailed walkthroughs and BIOS update notes for the most common motherboard brands:
Once your PC reads UEFI + Secure Boot On with a ready TPM 2.0, you’re set for the beta and for day one.


