Unexpected mouse movements, new user accounts, or programs opening on their own can signal that someone is remotely accessing your Windows 11 PC. Identifying and stopping unauthorized remote sessions quickly reduces the risk of data theft, privacy invasion, and further system compromise. Below, you’ll find detailed instructions to check for remote access, confirm suspicious activity, and secure your PC against future threats.
Check for Remote Access Using Windows Event Viewer
Step 1: Open Event Viewer by searching for it in the Windows Search bar and selecting the matching result. Event Viewer logs system activity, including remote access attempts.
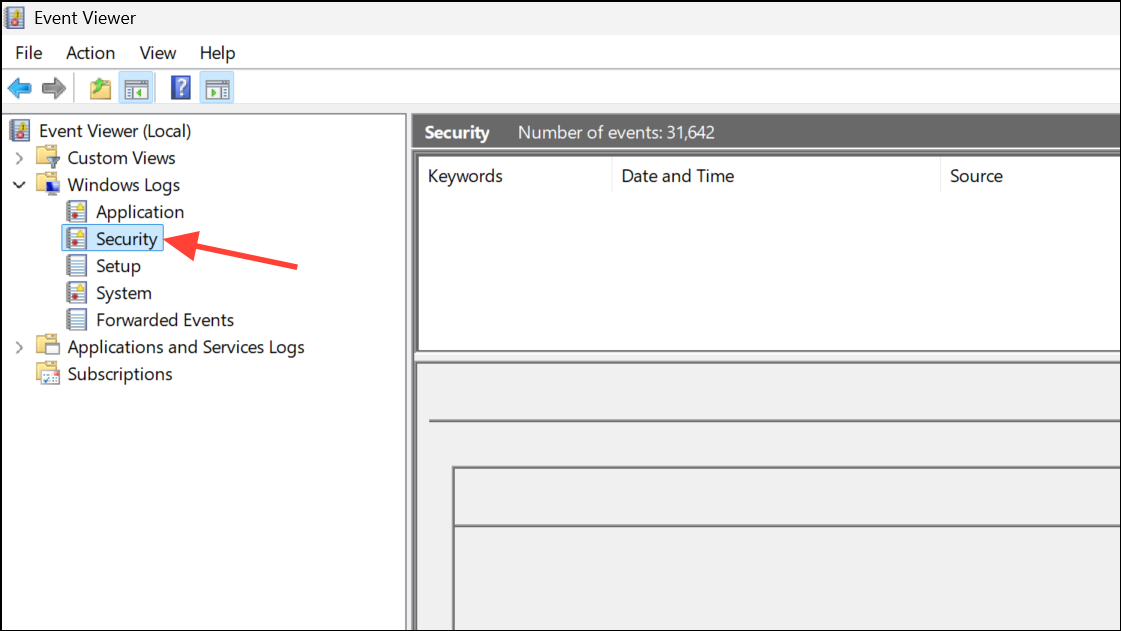
Step 2: Navigate to Windows Logs → Security in the left sidebar. This section records logon events and security-related actions.
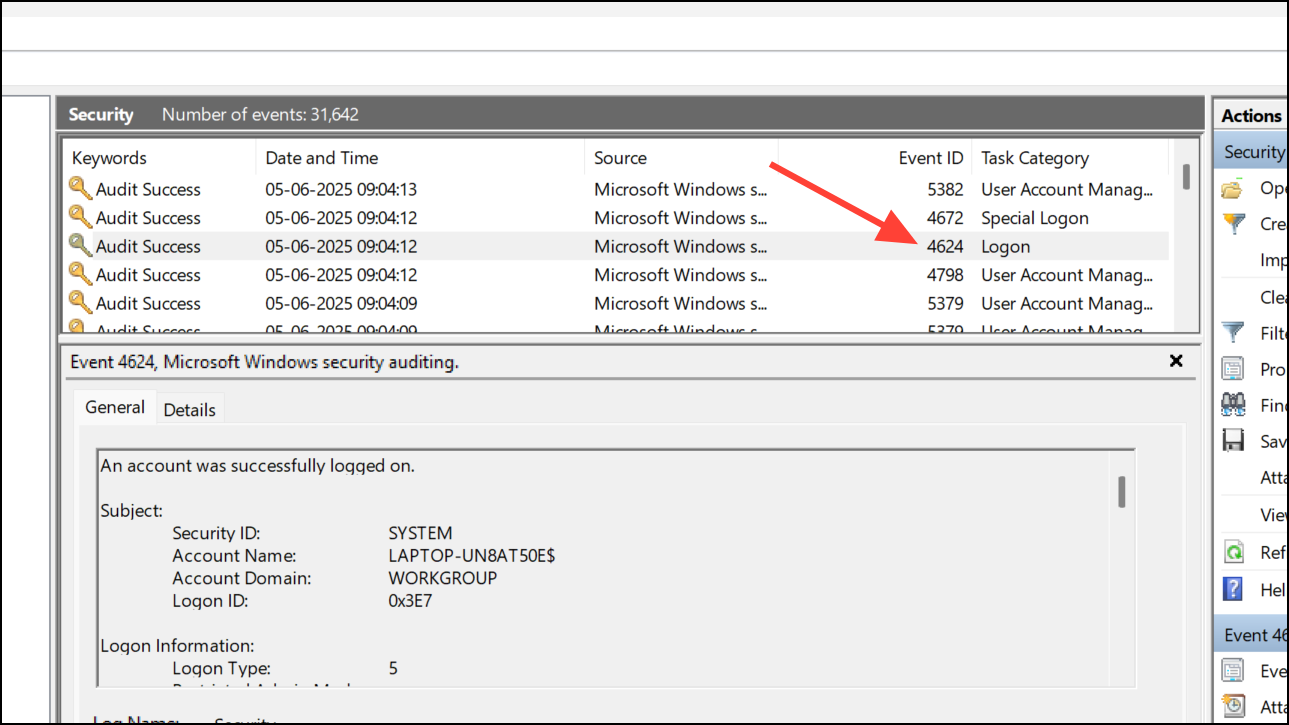
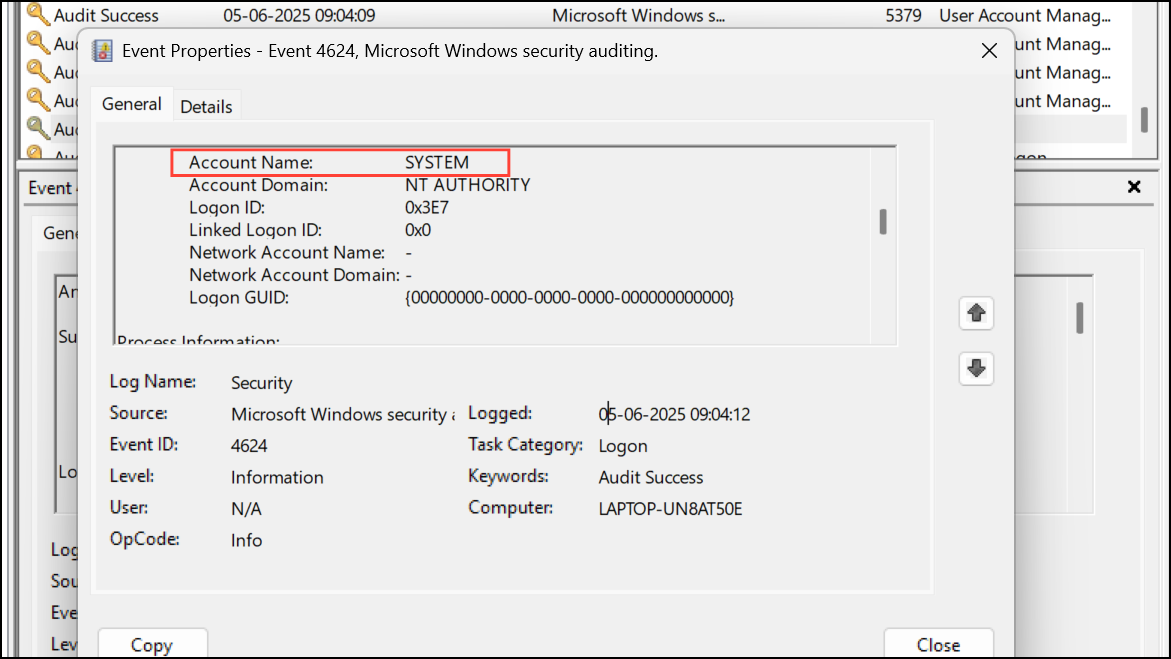
Step 3: Click the Event ID column to sort events numerically. Look for Event ID 4624, which indicates a successful logon.
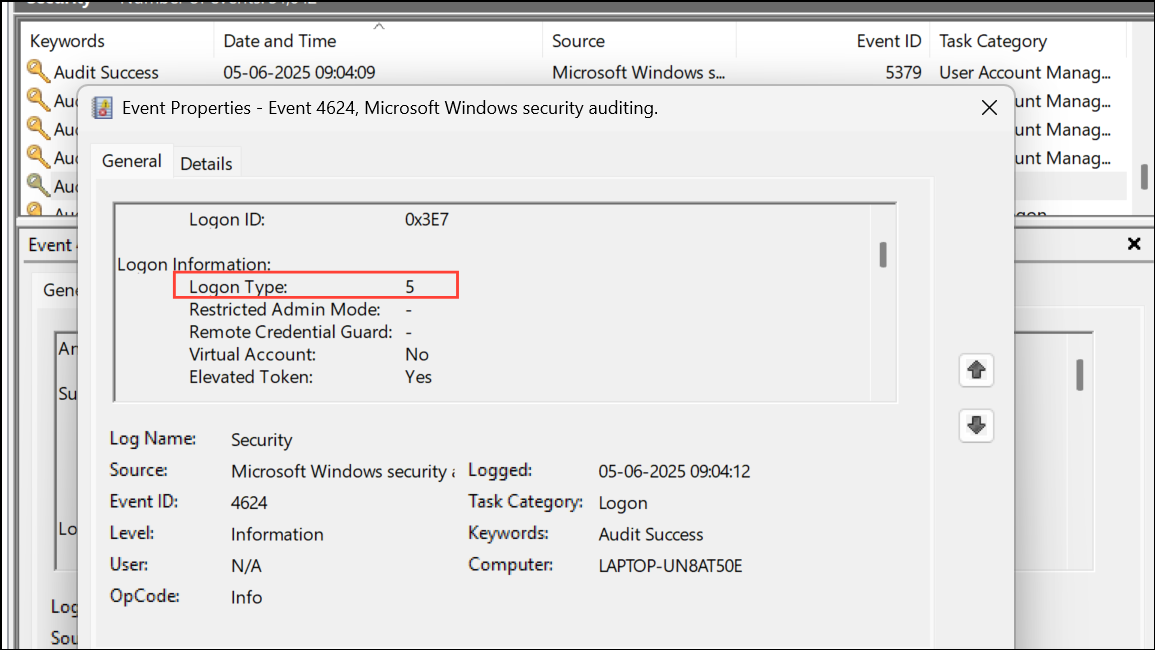
Step 4: Double-click each 4624 event and check the details for Logon Type 10. Logon Type 10 is specifically used for Remote Desktop (RDP) connections. If you see this logon type and you did not initiate a remote session, it suggests someone accessed your PC remotely.
Step 5: Review the Account Name and Source Network Address fields to identify which account was used and where the connection originated.
Identify Active Remote Sessions with Command Prompt
Step 1: Launch Command Prompt by pressing Windows + R, typing cmd, and pressing Enter.
Step 2: To see who is currently logged in locally, type:
query user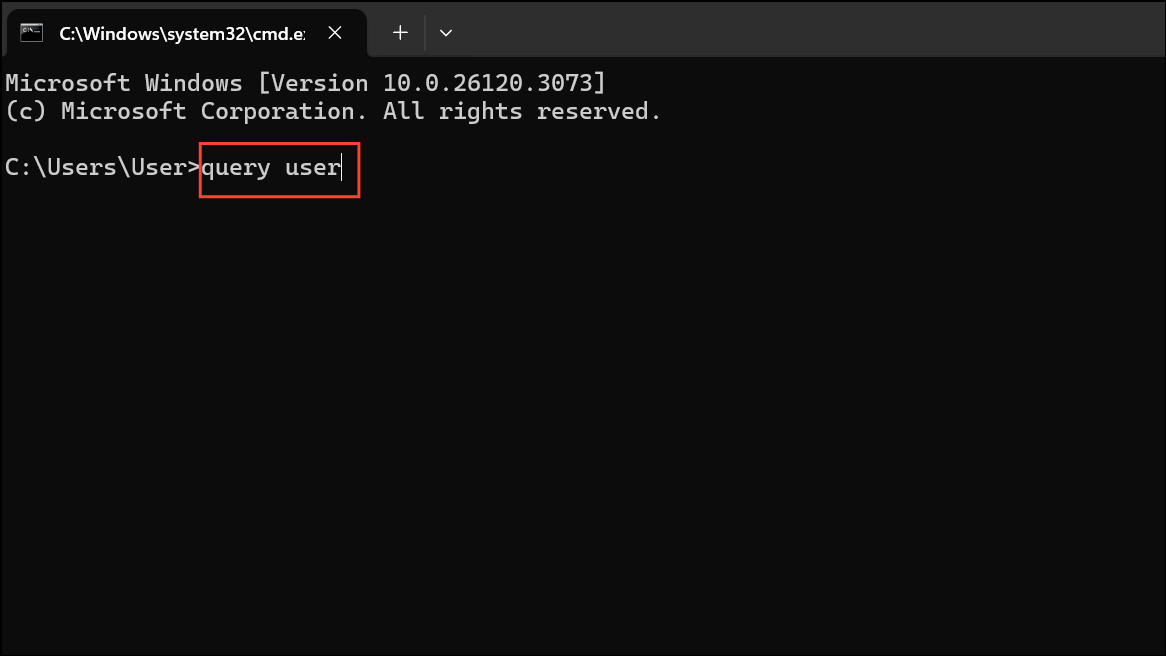
This command lists all active user sessions, their logon times, and session states.
Step 3: To check remote sessions on another PC (if you have permissions), use:
query user /server:ComputerName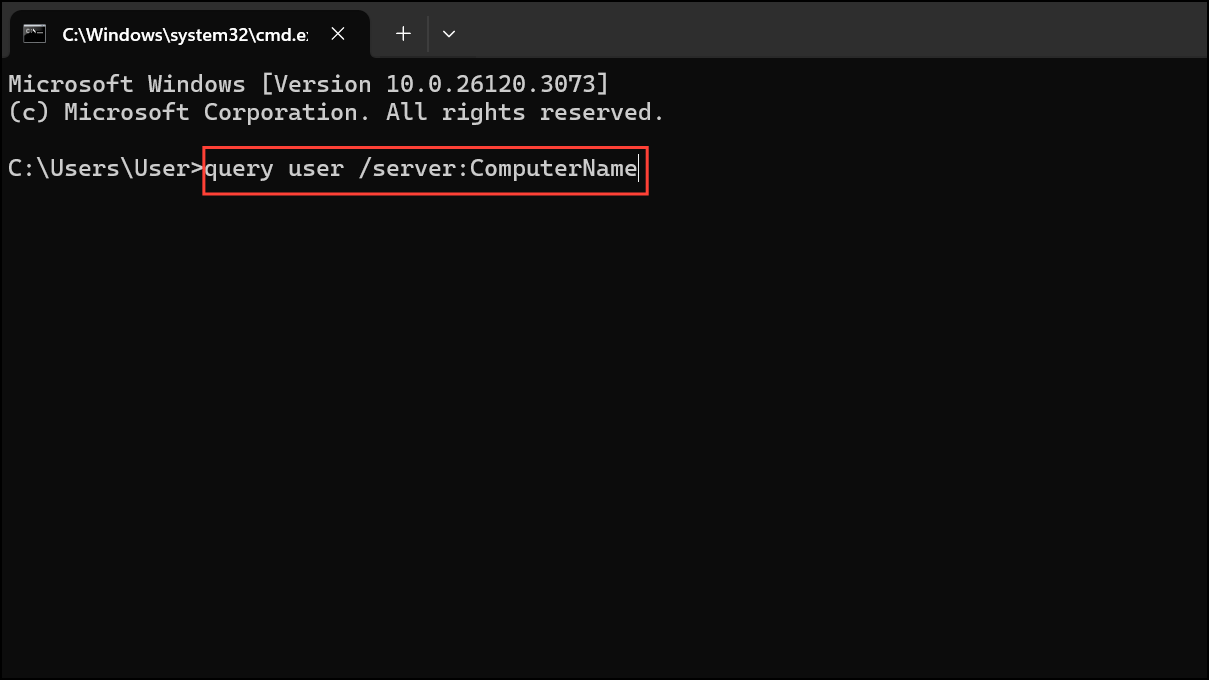
Replace ComputerName with the actual name of the remote PC. This displays active sessions, including users connected via Remote Desktop.
Step 4: If you prefer PowerShell, open it and use:
quser /server:ComputerName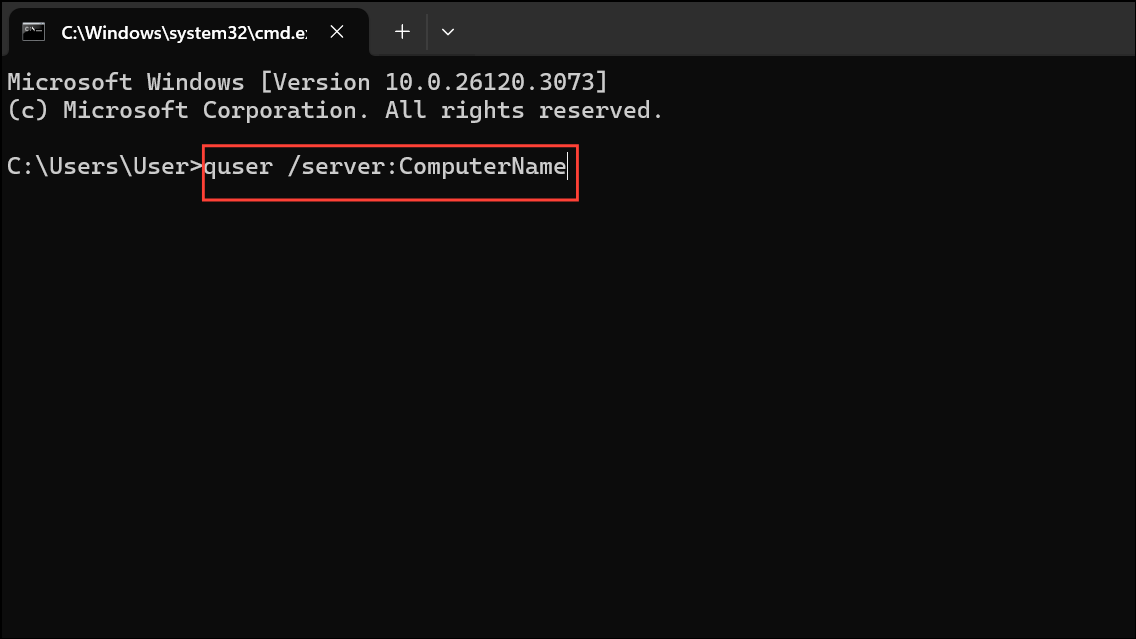
Both methods reveal which users are connected, helping you spot unauthorized remote access in real time.
Monitor Remote Desktop Settings and User Permissions
Step 1: Open Windows Settings by pressing Windows + I. Select System from the left menu, then scroll to and click Remote Desktop.
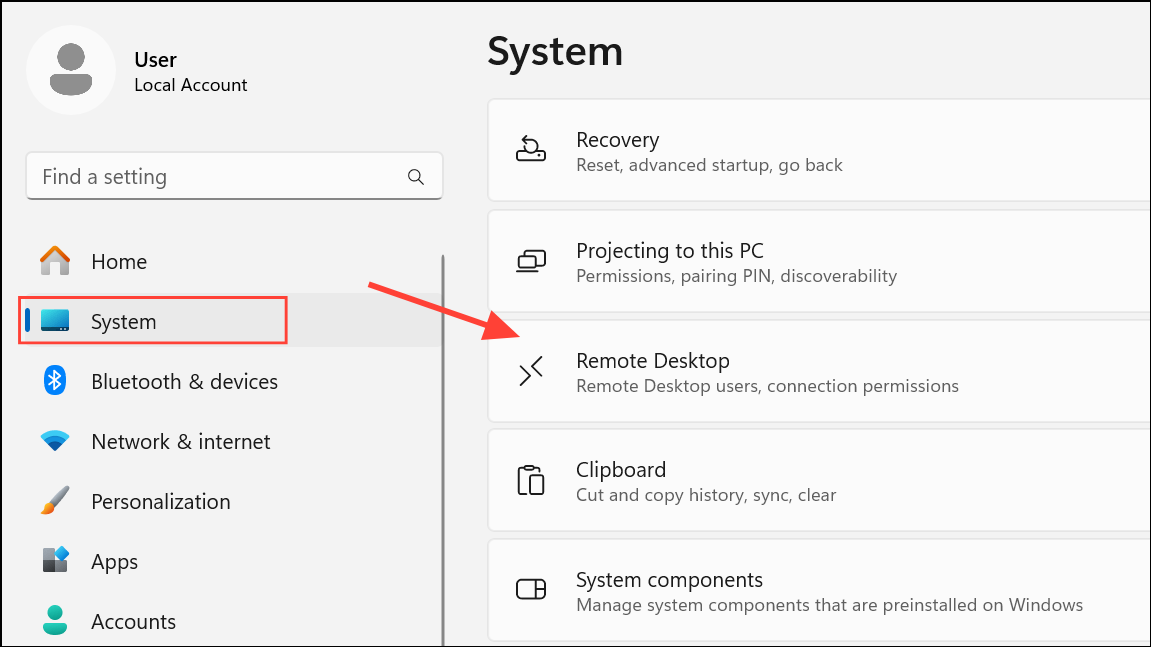
Step 2: Check if Remote Desktop is enabled. If it’s on and you did not activate it, this could indicate unauthorized configuration changes.
Step 3: Click the arrow next to Remote Desktop users to view the list of accounts permitted to access your PC remotely. Remove any unfamiliar users by selecting them and choosing Remove.
Step 4: To block all future remote desktop connections, toggle the Remote Desktop switch to Off. This immediately prevents new remote sessions.
Detect Unusual Activity and Suspicious Programs
Step 1: Open Task Manager by pressing Ctrl + Shift + Esc or right-clicking the Start button and selecting Task Manager.
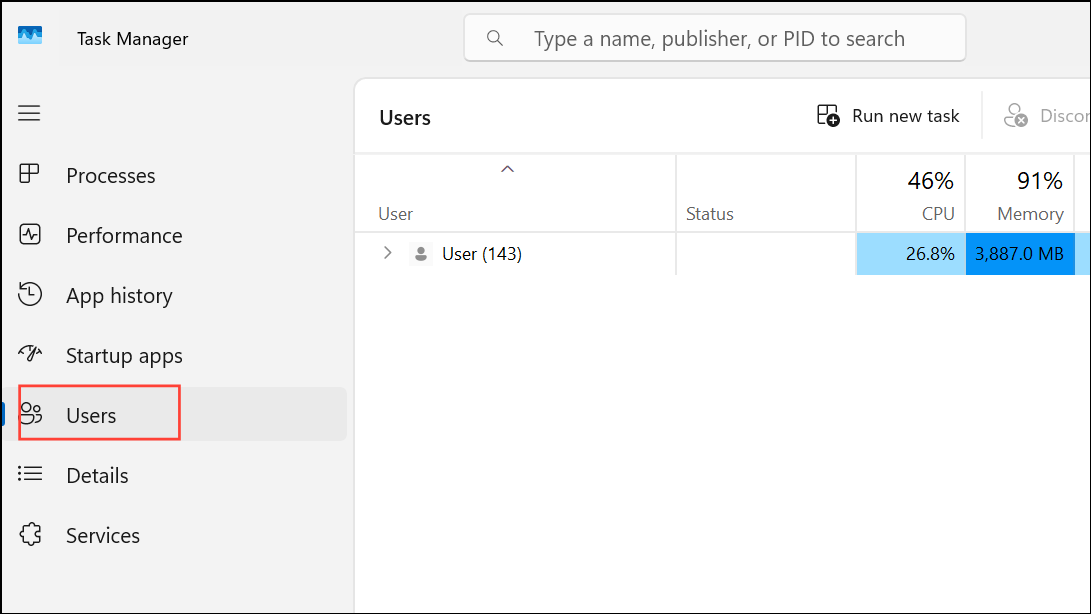
Step 2: Go to the Users tab to see all accounts currently logged in. Unexpected user sessions may indicate remote access.
Step 3: Check the Processes tab for unfamiliar or suspicious applications, especially those associated with remote access tools such as TeamViewer, AnyDesk, VNC, or Chrome Remote Desktop. If you find programs you didn’t install, right-click and select End Task, then uninstall them via Windows Settings.
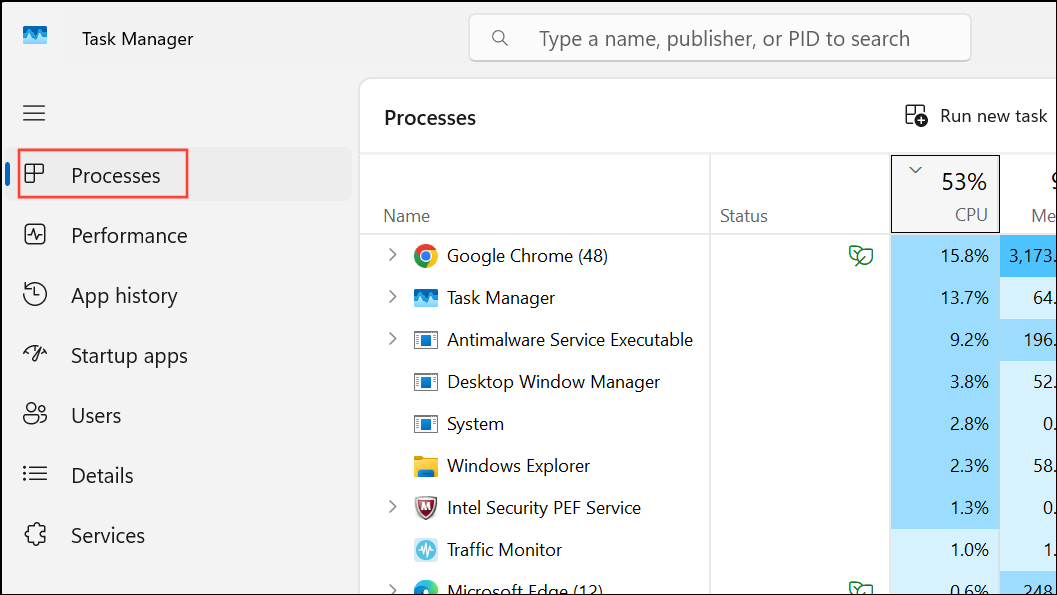
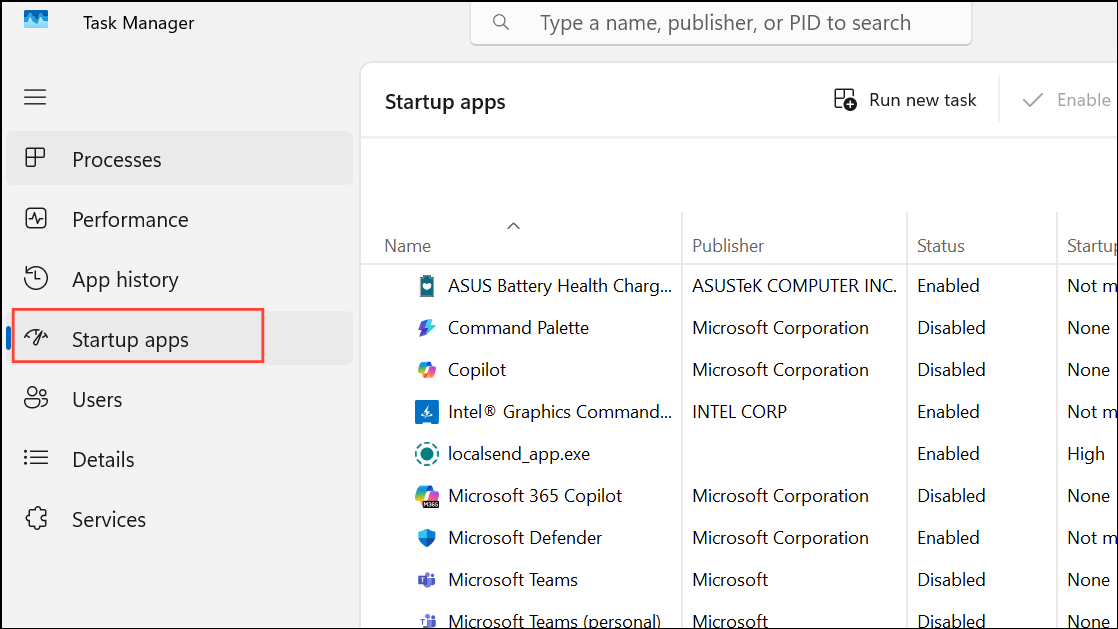
Step 4: Review the Startup apps tab for unknown programs set to launch at boot. Disable any entries you do not recognize.
Track Network Connections for Suspicious Activity
Step 1: Open Command Prompt and enter:
netstat -ano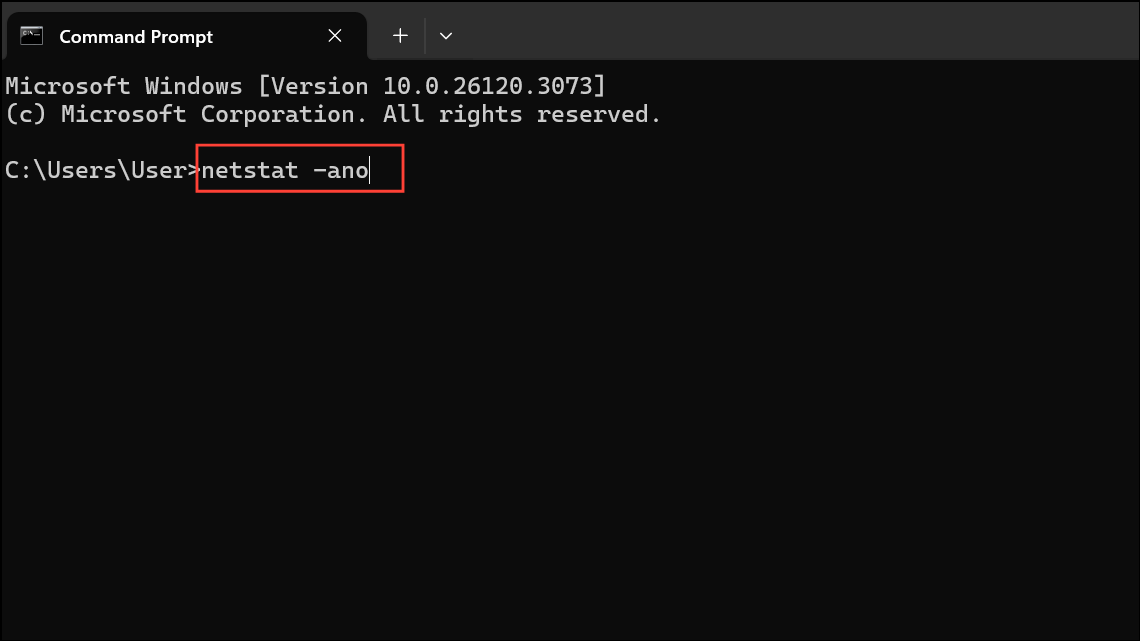
This command lists all active network connections along with their process IDs (PIDs).
Step 2: Look for connections on common remote access ports such as 3389 (RDP), 5900 (VNC), 5938 (TeamViewer), 6568 (AnyDesk), and 8200 (GoToMyPC). Unusual or persistent connections on these ports may indicate remote access.
Step 3: Match any suspicious PID to the corresponding process in Task Manager by enabling the PID column in the Details tab. Investigate or terminate unknown processes as needed.
Audit User Accounts and Scheduled Tasks
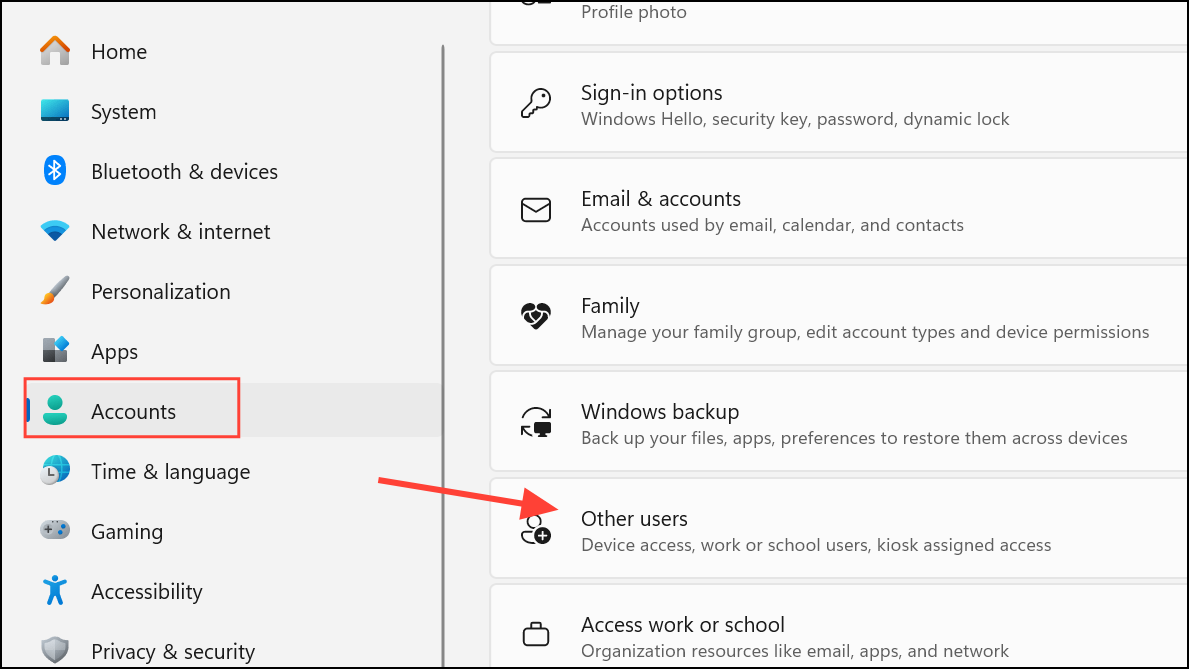
Step 1: Open Settings → Accounts → Family & other users. Review the list of user accounts. Remove any that you did not create, as attackers sometimes add accounts for persistent access.
Step 2: Open Task Scheduler by searching for it in the Start menu.
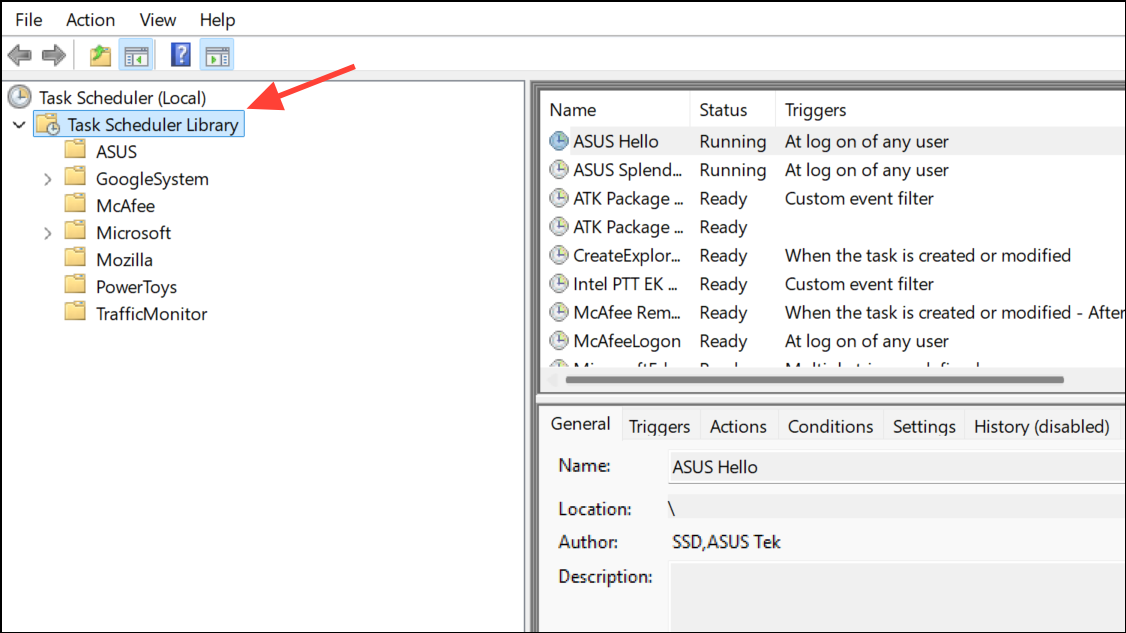
Step 3: In the left panel, expand Task Scheduler Library. Look for tasks or folders with unfamiliar names. Right-click and select Properties to check the Actions and Triggers tabs. Tasks launching unknown programs or scripts can be a sign of malware-driven remote access.
Run Antivirus and Remove Remote Access Tools
Step 1: Disconnect your PC from the internet as soon as you suspect a remote intrusion. This immediately severs active remote sessions and limits further unauthorized actions.
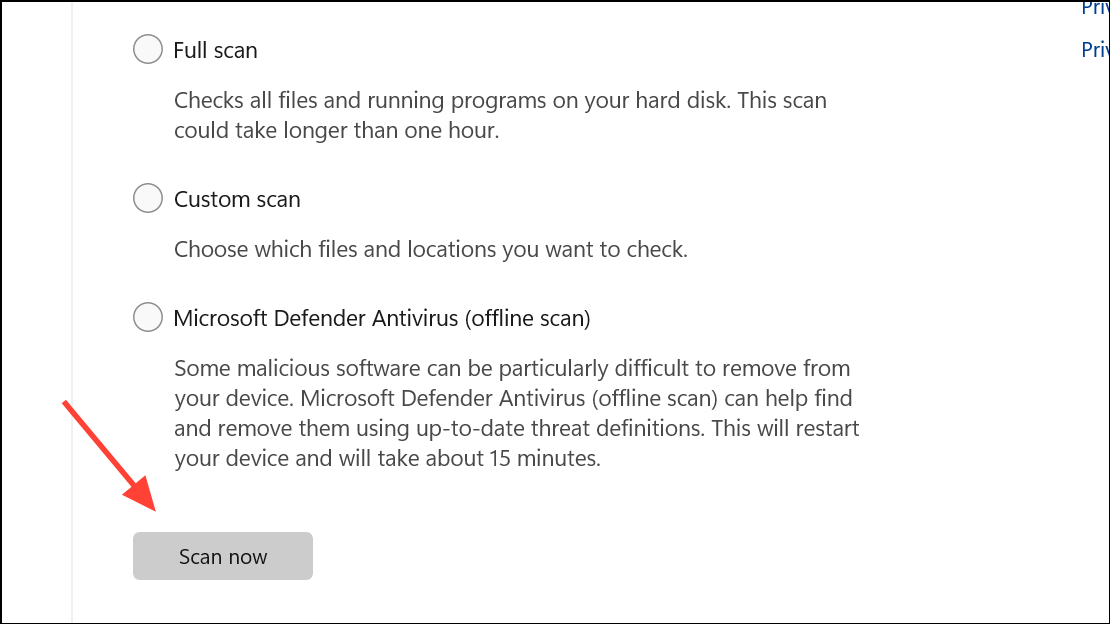
Step 2: Use Windows Security by searching for Windows Security in the Start menu. Go to Virus & threat protection → Scan options, select Microsoft Defender Antivirus (offline scan), and click Scan now. This scan checks for advanced threats such as rootkits that may evade standard scans.
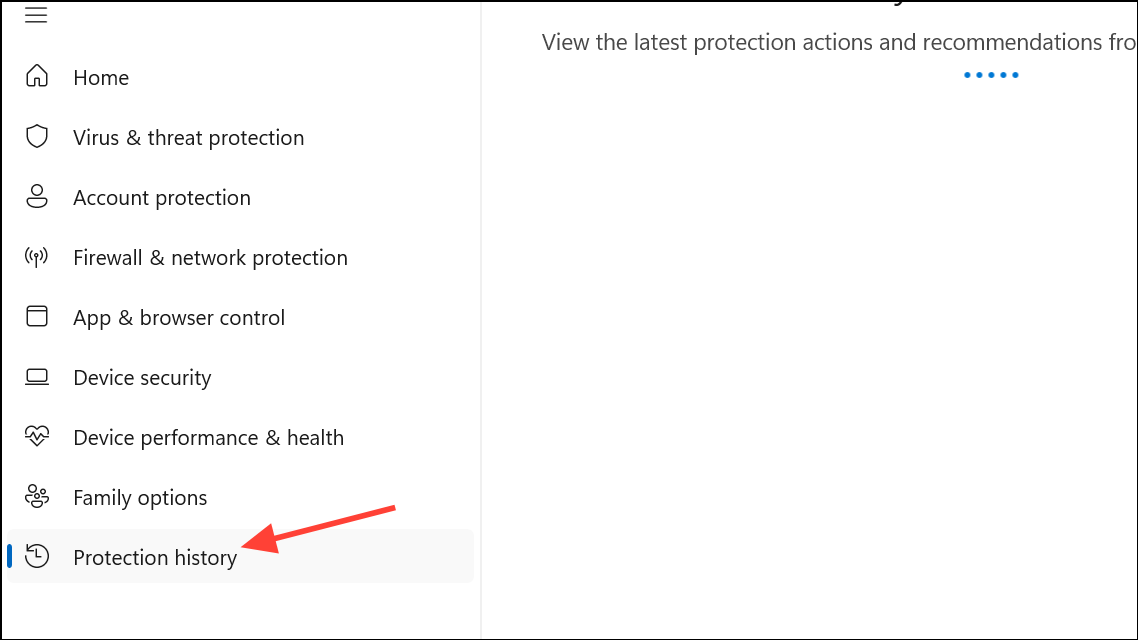
Step 3: After the scan, review Protection history for detected threats and follow prompts to remove them.
Step 4: Manually uninstall any remote access tools you don’t use or recognize by going to Settings → Apps → Installed apps and removing suspicious entries. Also, check your browser extensions for unfamiliar add-ons and remove them.
Block Remote Access Ports in Windows Firewall
Step 1: Search for Windows Defender Firewall with Advanced Security in the Start menu and open it.
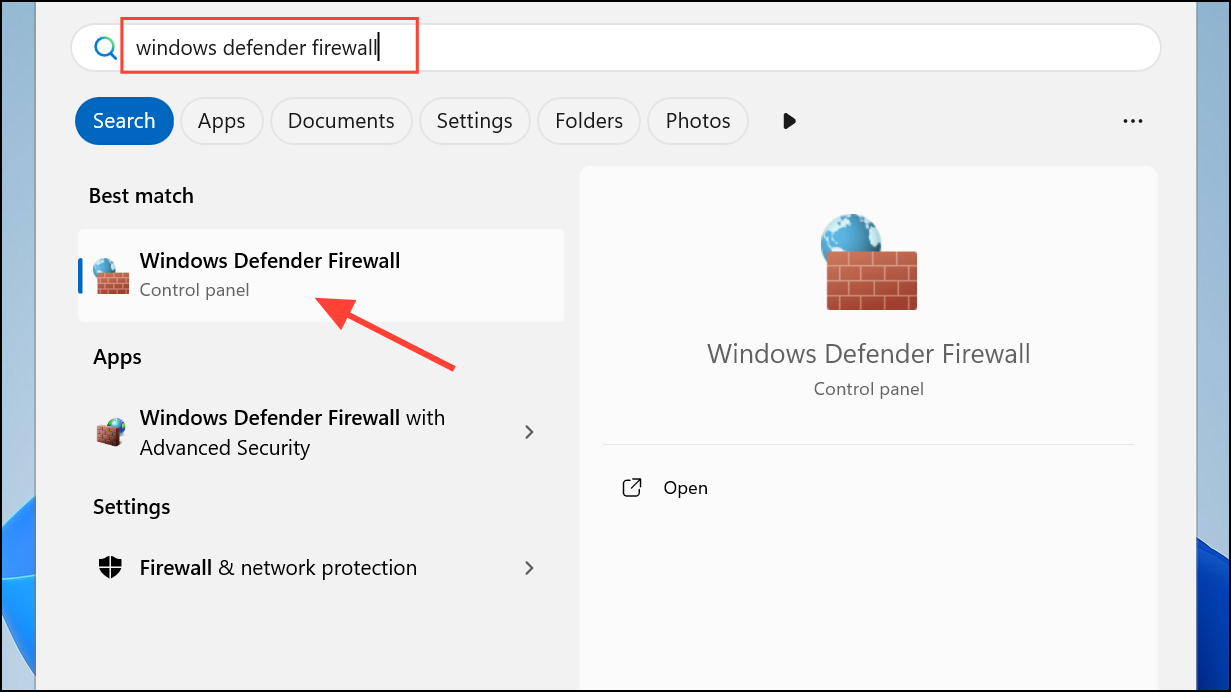
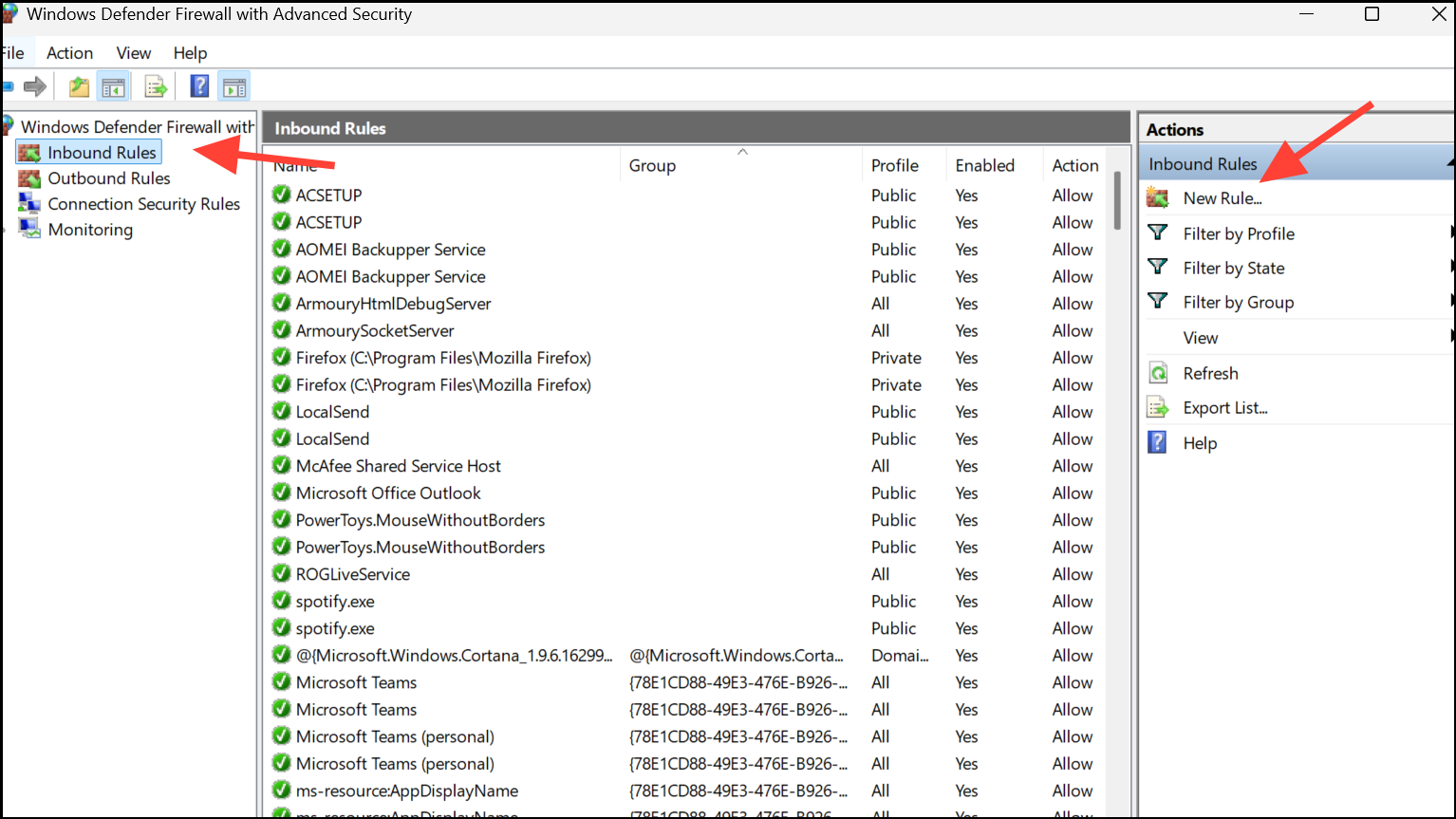
Step 2: Click Inbound Rules in the left pane, then select New Rule on the right.
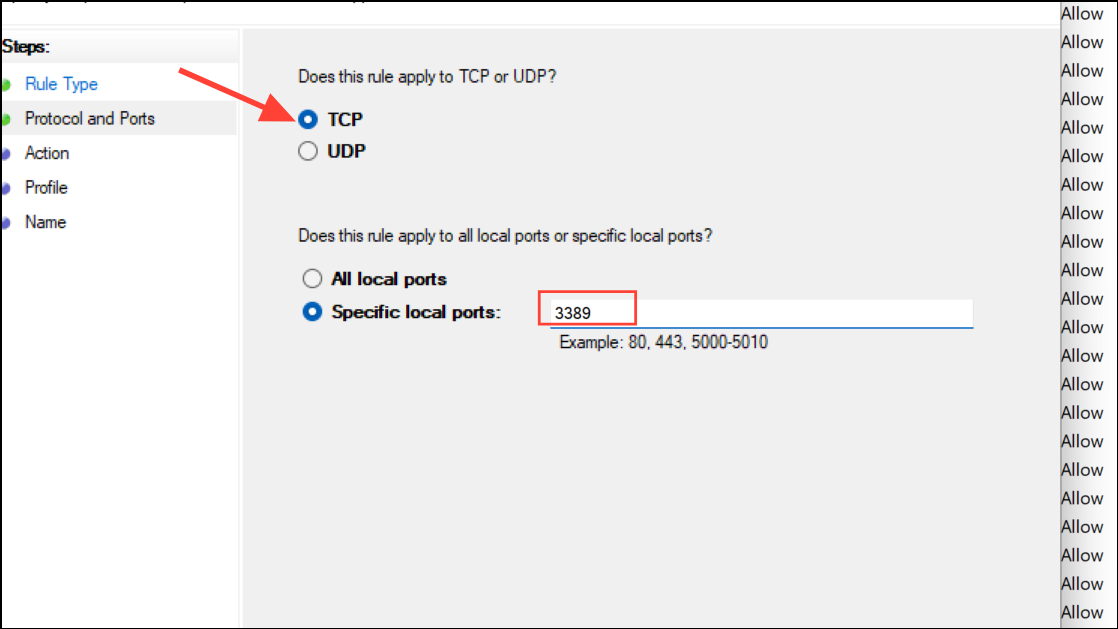
Step 3: Choose Port and click Next. Select TCP and enter a port number associated with remote access (e.g., 3389 for RDP).
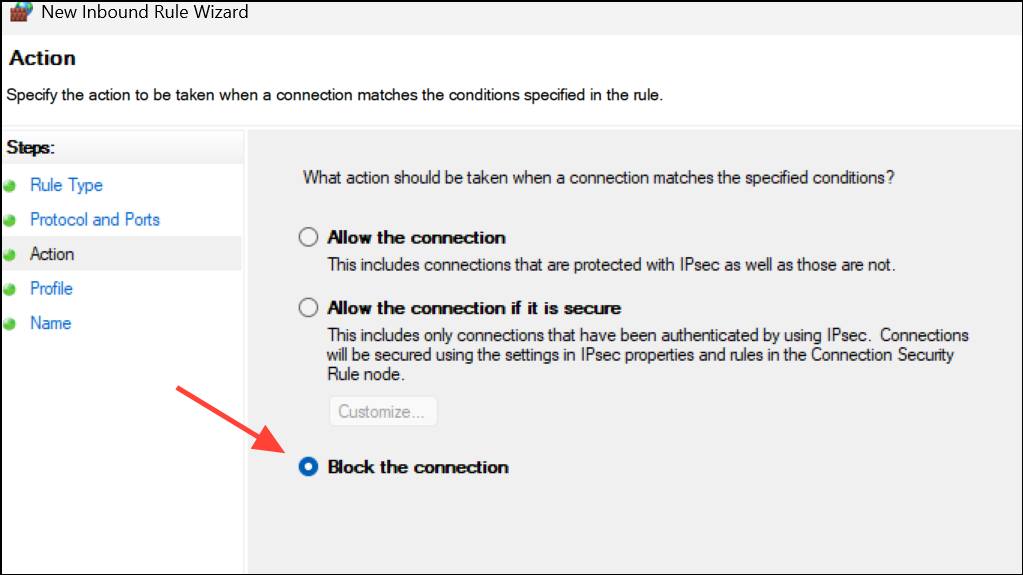
Step 4: Select Block the connection, click Next, and complete the rule setup. Repeat for each port you wish to block. Assign clear names to each rule for easy identification.
This step prevents new remote connections on the specified ports, reducing the risk of future unauthorized access.
Perform a Clean Windows Installation (If Necessary)
Step 1: If malware persists or you continue to see suspicious activity after following the above steps, consider performing a clean Windows install. Back up important files to an external drive, avoiding cloud storage if you suspect infection.
Step 2: Download the latest Windows installation media from Microsoft’s official website. Boot from the installation media and choose the option to perform a clean install, which erases all data and resets your system to a secure state.
This step is a last resort but is highly effective at removing persistent threats that evade detection or removal.
Regularly monitoring your system for unusual activity, keeping your security software updated, and limiting remote access permissions significantly reduces your risk of unauthorized remote access. Staying proactive with these checks helps you maintain control and privacy over your Windows 11 PC.


