Restricting which programs can run on a Windows 11 system prevents unauthorized software, reduces malware risk, and improves compliance with organizational policies. Administrators and home users can accomplish this by whitelisting (allowing only specified apps) or blacklisting (blocking specific apps) through several built-in Windows features and management tools. The most effective method leverages application whitelisting, which only permits approved applications while blocking all others, but there are also targeted approaches for blacklisting and managing app access.
Whitelisting Programs Using AppLocker
AppLocker is available on Windows 11 Pro, Enterprise, and Education editions. It lets administrators define which executable files, installer packages, scripts, and packaged apps are allowed or blocked. This method is highly effective for organizations or anyone who needs strict control over application usage.
Step 1: Open the Local Security Policy tool. Press the Windows key, type secpol.msc, and press Enter. This launches the Local Security Policy editor.
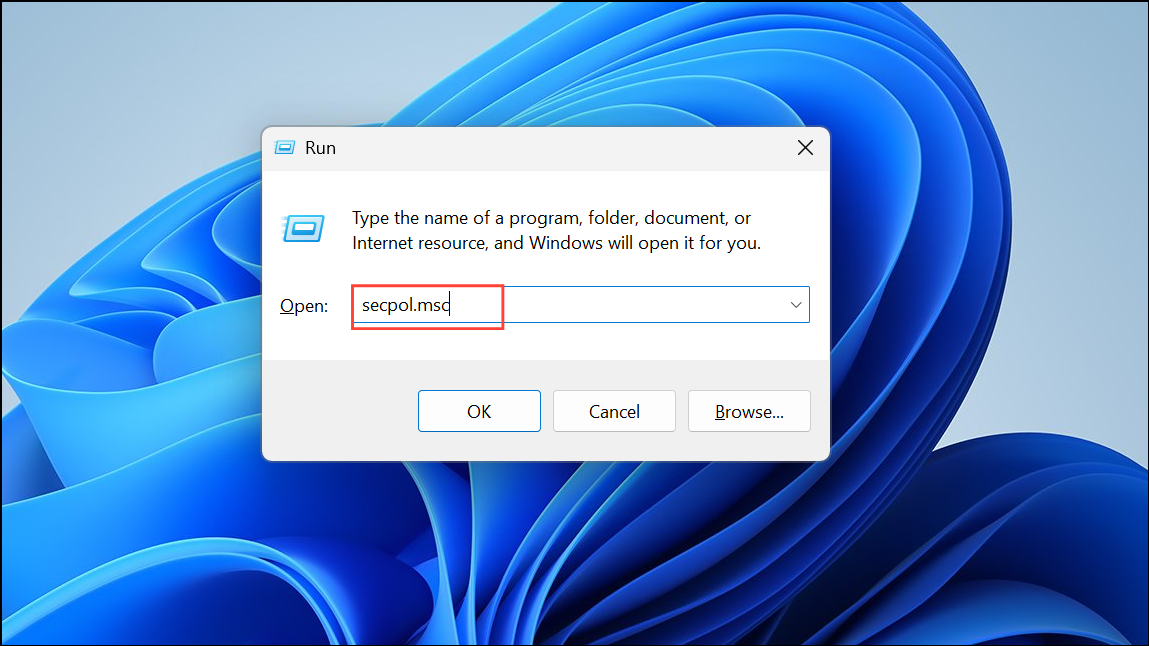
Step 2: In the left pane, expand Application Control Policies and select AppLocker. Four rule types appear: Executable Rules, Windows Installer Rules, Script Rules, and Packaged App Rules.
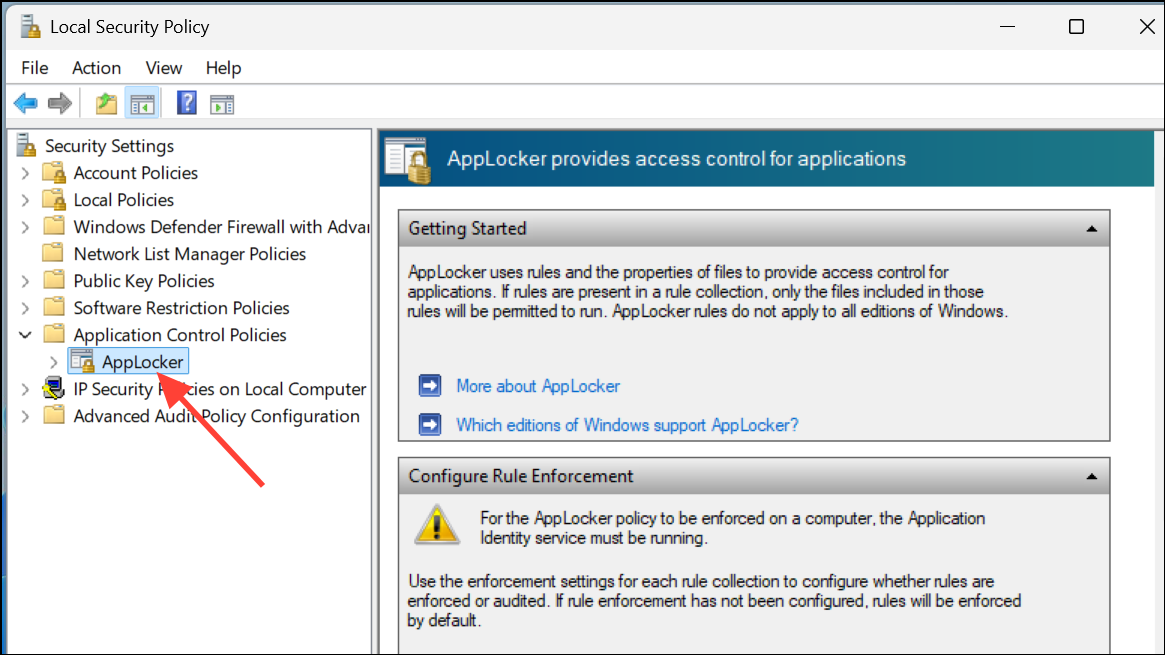
Step 3: Right-click Executable Rules and choose Create Default Rules to allow standard Windows applications and block all others. For more granular control, right-click again and select Automatically Generate Rules, then specify the folders (like C:\Program Files) containing apps you want to permit. The wizard will create rules for all programs found in those directories.
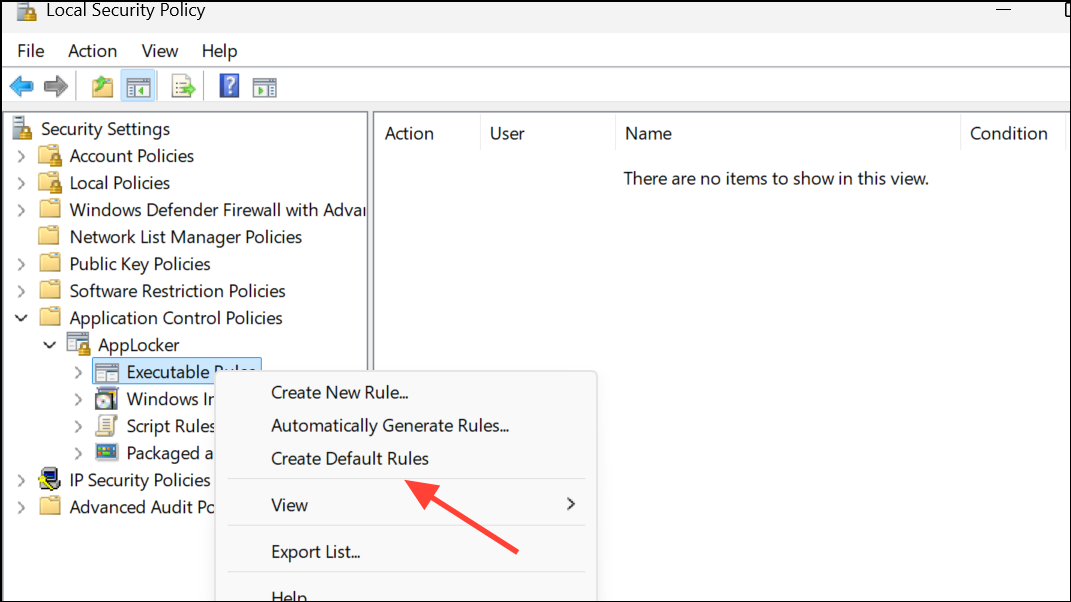
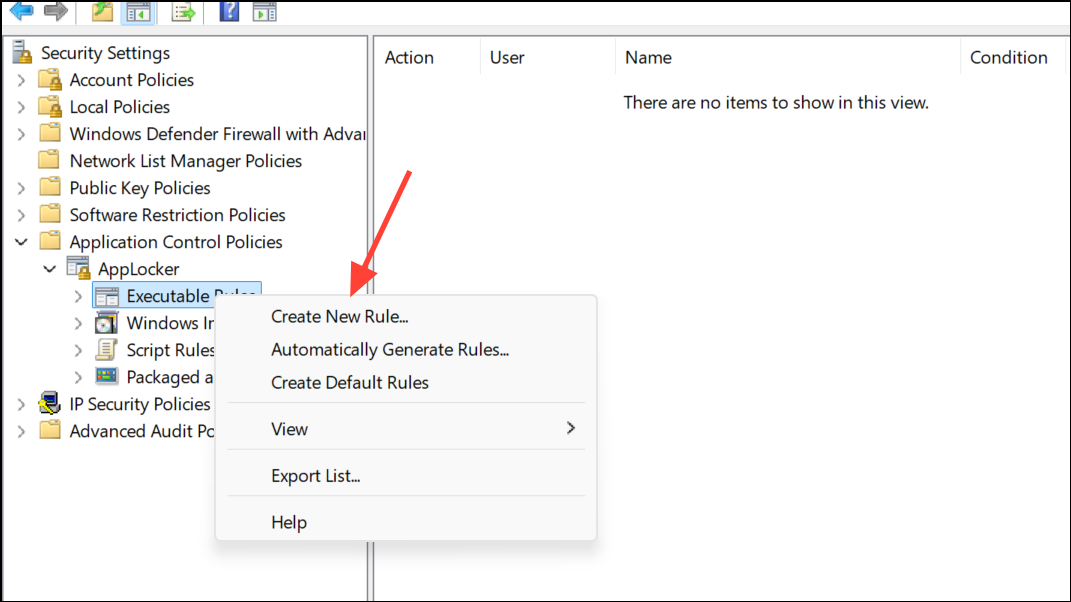
Step 4: To block or allow additional programs, right-click the relevant rule type and select Create New Rule. Follow the wizard to specify the program’s path, publisher, or file hash, and set the action to Allow or Deny.
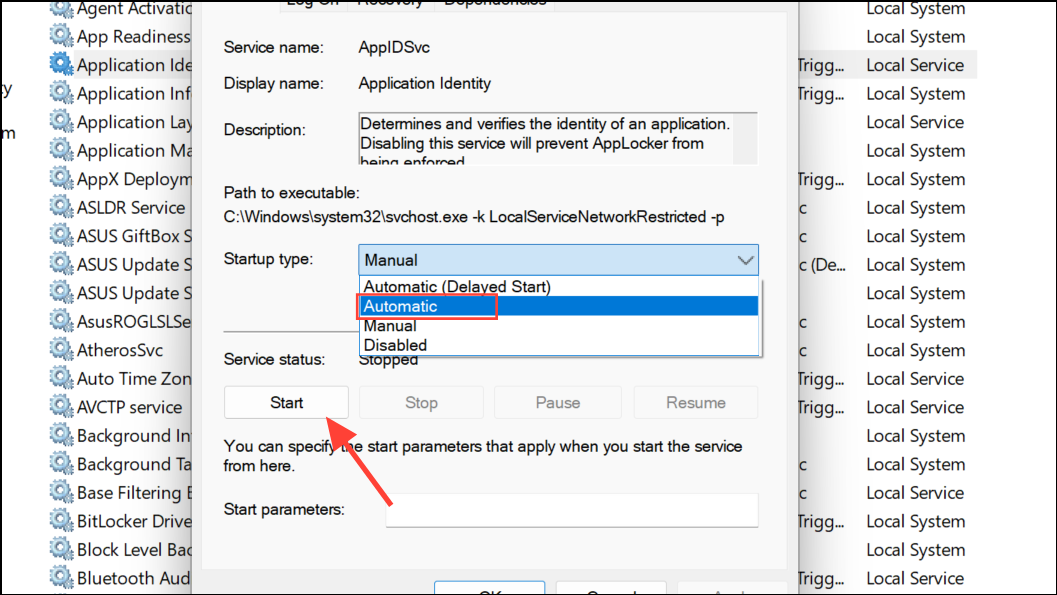
Step 5: Ensure the Application Identity service is running. Open services.msc, find Application Identity, double-click it, and click Start. Set the startup type to Automatic if you want rules enforced on every reboot.
With AppLocker configured, only whitelisted programs can run. Attempts to launch blocked or unlisted applications result in a system administrator error message.
Blacklisting Programs Using Group Policy
For situations where you want to block specific applications but allow others, use the “Don’t run specified Windows applications” policy in the Group Policy Editor. This approach is suitable for targeted restrictions rather than broad lockdowns.
Step 1: Open the Group Policy Editor by pressing Windows + R, typing gpedit.msc, and pressing Enter.
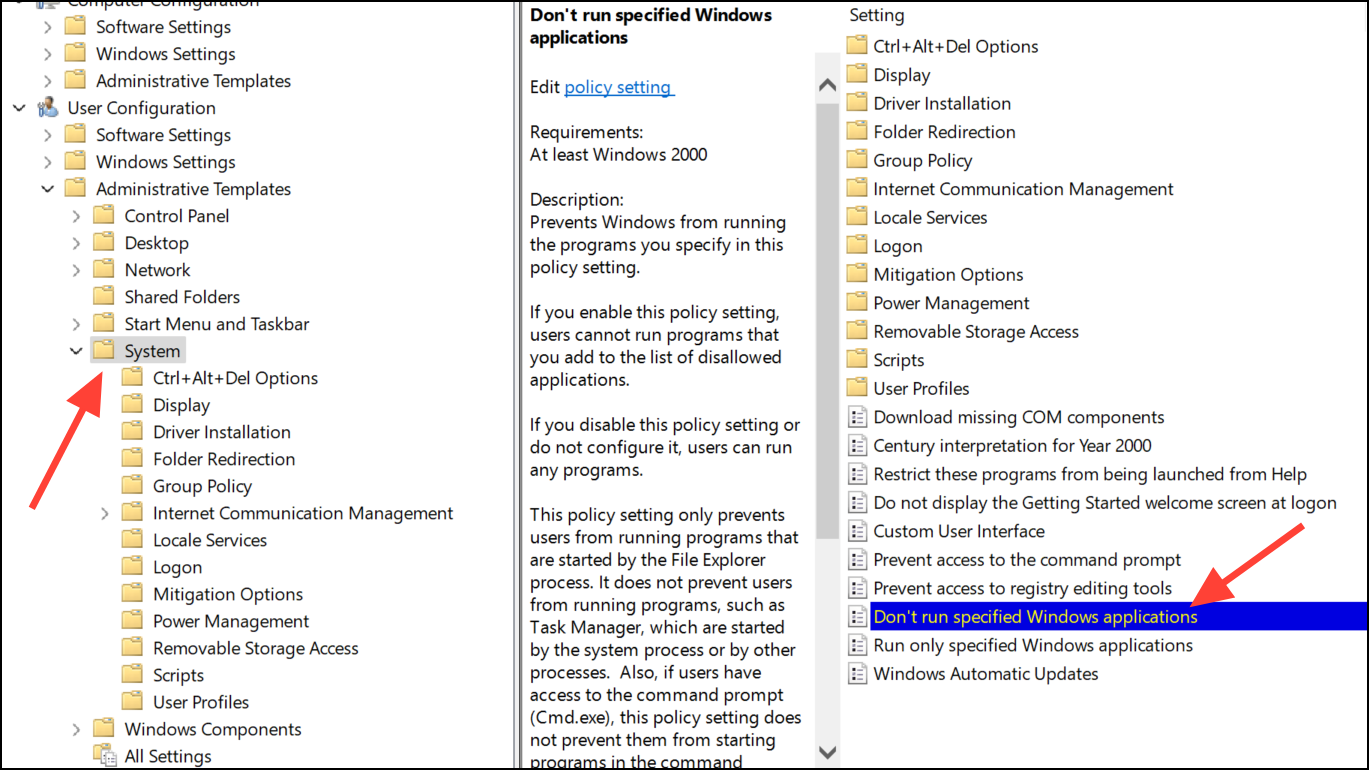
Step 2: Navigate to User Configuration > Administrative Templates > System, then double-click Don’t run specified Windows applications.
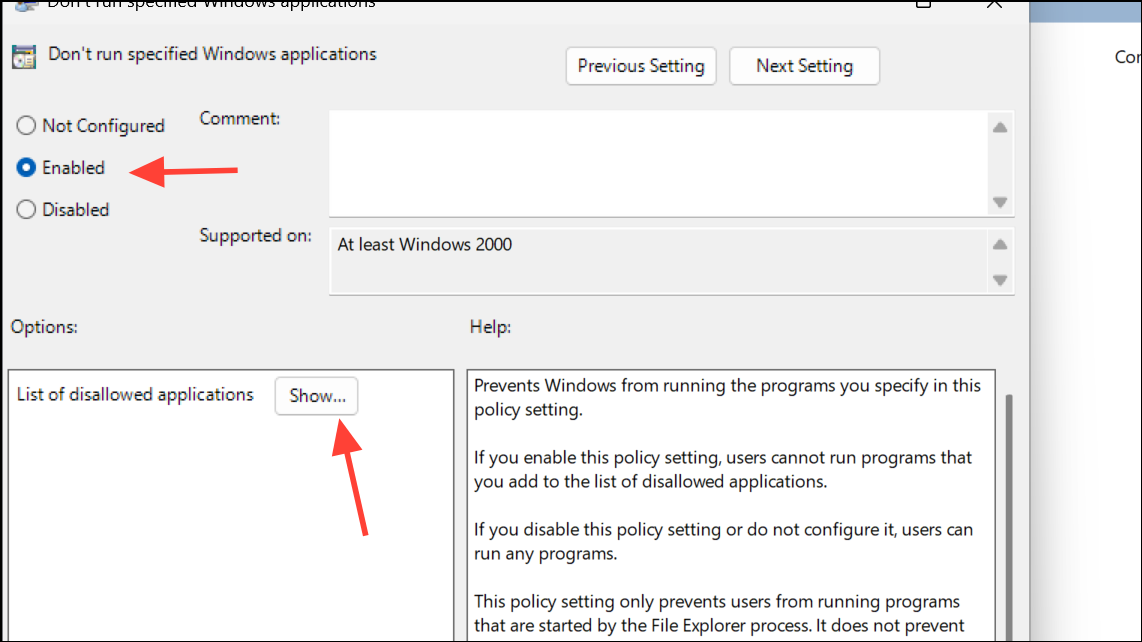
Step 3: Set the policy to Enabled, then click Show and enter the names of executables you want to block (for example, notepad.exe or firefox.exe).
Step 4: Click OK to apply the settings. The specified apps will now be blocked for the user or group targeted by this policy.
Whitelisting Programs with Software Restriction Policies
Software Restriction Policies (SRP) provide another option for controlling application execution. This feature is available in Windows Pro and Enterprise editions and is managed via the Local Security Policy editor.
Step 1: Launch the Local Security Policy tool (secpol.msc).

Step 2: Expand Software Restriction Policies in the left pane. If no policy exists, right-click and select Create New Policy.
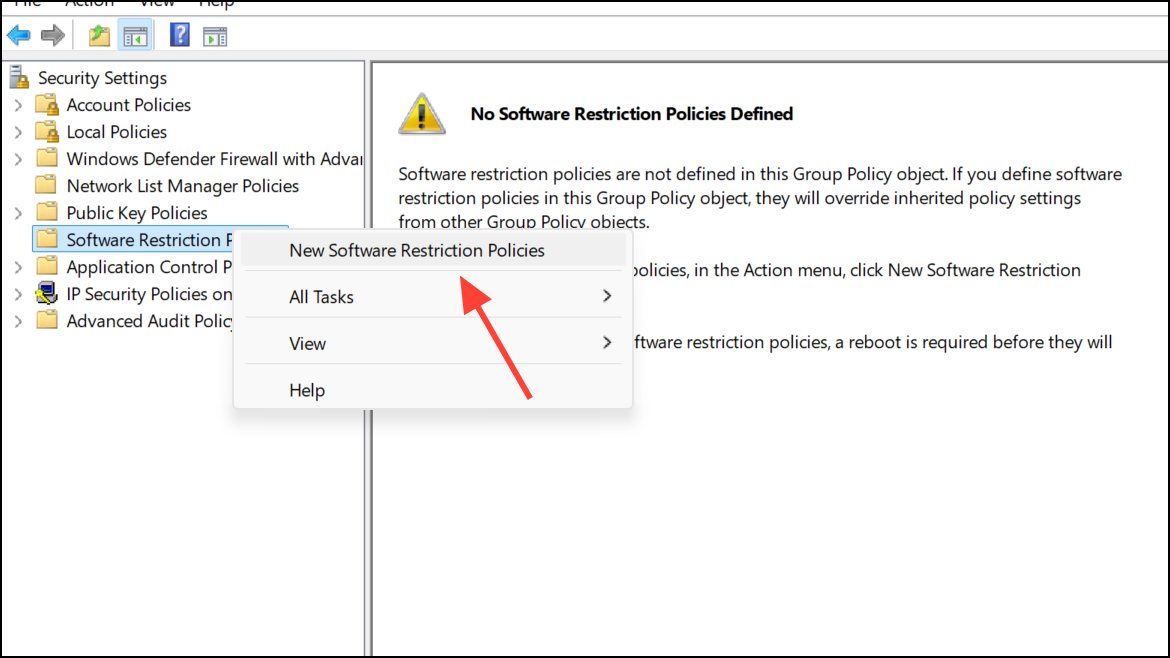
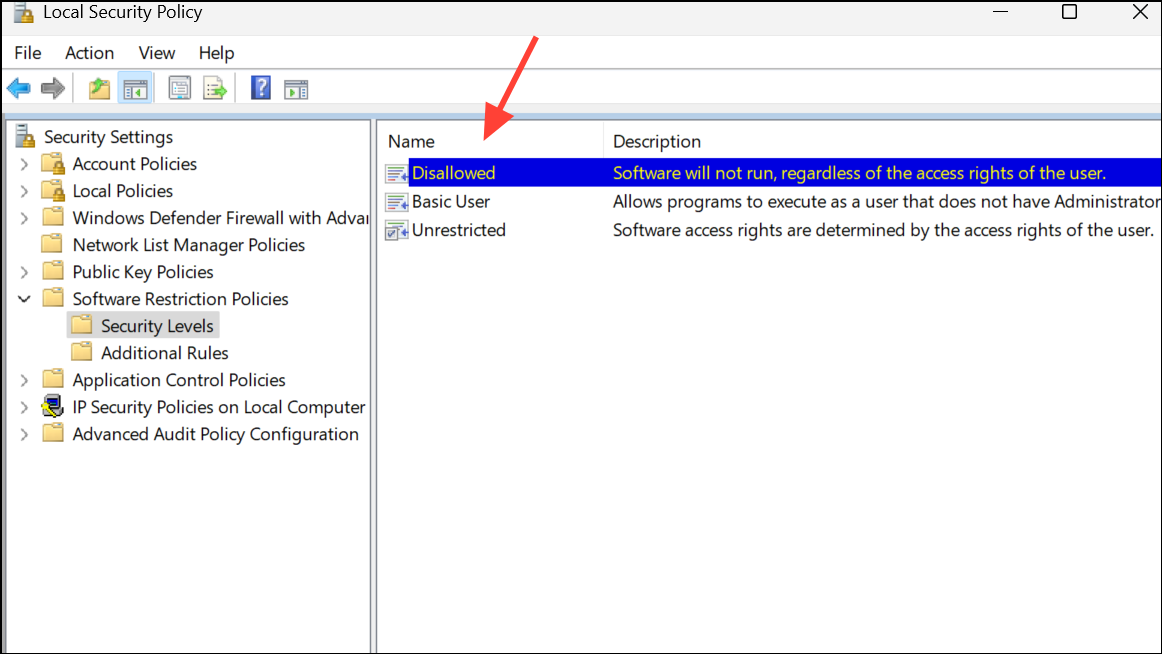
Step 3: Set the default security level to Disallowed so all programs are blocked except those you explicitly allow.
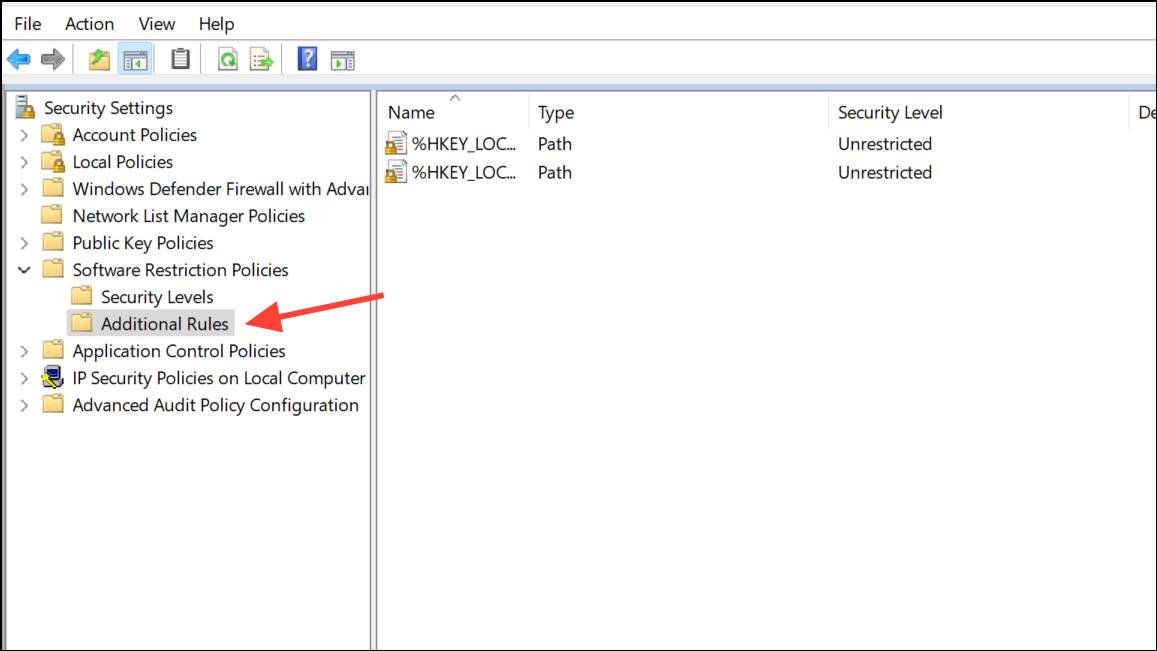
Step 4: Under Additional Rules, create Path, Hash, or Certificate rules for each application or folder you want to permit.
This method is effective for basic allowlisting, but AppLocker is more flexible and recommended for newer Windows versions.
Managing Applications with Microsoft Intune
Organizations using Microsoft Intune can enforce application restrictions across managed devices. Intune policies can define which apps are approved for installation and block others, and can integrate with AppLocker and Windows Defender Application Control (WDAC) for advanced scenarios.
Step 1: In the Microsoft Endpoint Manager admin center, go to Apps > App protection policies to define approved applications.
Step 2: Use Endpoint Security > Attack surface reduction to set up application control or browser control policies for Windows devices.
Step 3: For more granular restrictions, configure AppLocker or WDAC policies within Intune and deploy them to targeted devices or users.
Step 4: To block non-admin installations from the Microsoft Store, set the Block non-admin user install policy or use the RequirePrivateStoreOnly registry key. This prevents users without admin rights from installing store apps, though enforcement can vary depending on app source and Windows version.
apps.microsoft.com in your firewall or proxy).Using Third-Party Tools for Application Control
Several free and commercial tools offer additional options for whitelisting or blacklisting applications:
- NoVirusThanks Driver Radar Pro: Controls which kernel drivers can load and allows for detailed application allowlisting.
- VoodooShield (now Cyberlock): Takes a snapshot of installed applications and blocks anything new unless explicitly allowed.
- AirDroid Business: Provides centralized app allowlist/blocklist management for organizations.
- CryptoPrevent: Adds allowlist entries for trusted programs, especially those that need to run from directories typically blocked by anti-malware tools.
These tools can supplement or, in some cases, replace built-in Windows features, especially for home users or small businesses.
Managing Microsoft Store App Installs
Windows 11 allows users to install apps from the Microsoft Store or directly from apps.microsoft.com. Blocking the Store app alone is not always sufficient, as web-based installers may bypass restrictions. To limit installations:
- Set RequirePrivateStoreOnly via Intune, Group Policy, or registry to restrict app installs to your organization's private store.
- Enable Block non-admin user install to prevent standard users from installing store apps.
- Consider disabling the InstallService (Install Service for Microsoft Store) to disrupt the installation process for store apps.
- Block access to
apps.microsoft.comat the network level for managed devices.
Due to ongoing changes in Microsoft Store delivery methods, test these settings thoroughly to confirm they block unwanted installations without disrupting approved workflows.
Controlling application access in Windows 11 is achievable with built-in tools like AppLocker, Software Restriction Policies, and Intune, as well as third-party solutions. Regularly review your allowlists and blocklists to keep your system secure and up to date.

