Monitoring software can be secretly installed on PCs by employers, parents, or malicious actors, often without obvious signs. These programs may record keystrokes, capture screenshots, track application use, or transmit data to third parties. Uncovering such software quickly is essential to protect personal information, maintain privacy, and avoid unauthorized surveillance. The following methods provide actionable steps to detect monitoring software, starting with the most reliable approaches.
Scan for Monitoring Software Using Antivirus and Anti-Malware Tools
Comprehensive system scans with reputable antivirus and anti-malware programs are the most effective way to uncover monitoring software. Many keyloggers, spyware, and employee monitoring tools are flagged as malicious or potentially unwanted programs (PUPs) by security software.
Step 1: Open your installed antivirus or anti-malware application. If you rely on built-in solutions, use Windows Defender on Windows or XProtect on macOS. Make sure virus definitions are fully updated to catch the latest threats.
Step 2: Select a full system scan rather than a quick scan. A full scan examines all files, including hidden and system folders where monitoring software may reside.
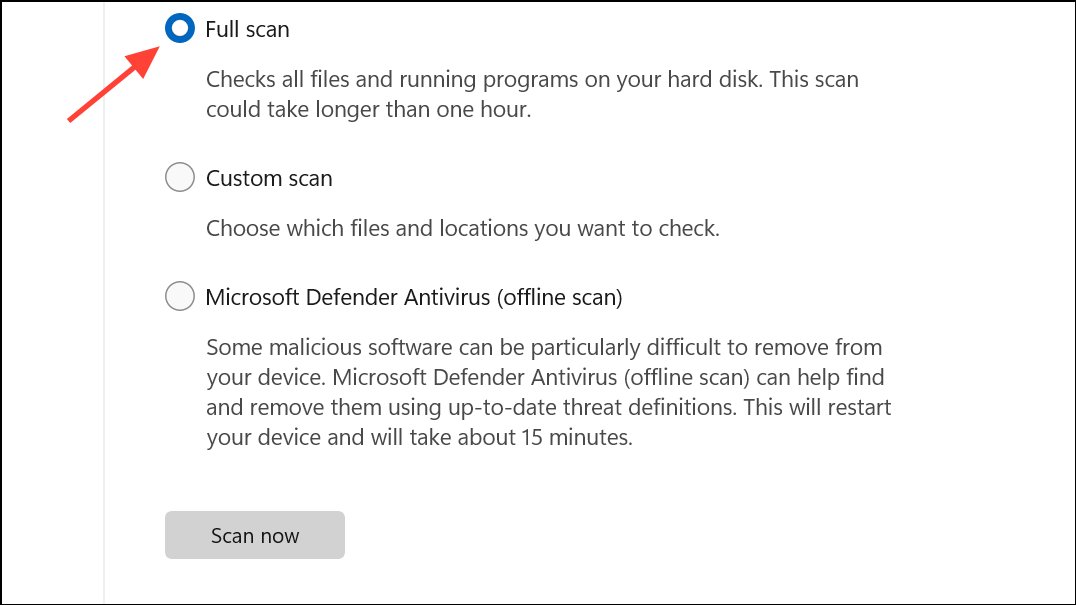
Step 3: Review the scan results. Pay close attention to any flagged items categorized as spyware, keyloggers, or remote access tools. Quarantine or remove these threats as directed by your security software.
Step 4: If your initial scan finds nothing but you still suspect monitoring, consider running a scan with a reputable third-party tool like Malwarebytes, Bitdefender, or similar. These programs may detect threats missed by default security tools.
Be aware that sophisticated monitoring software may attempt to evade detection by disabling antivirus functions or adding itself to exclusion lists. Regularly check your antivirus exclusions for unfamiliar entries and remove any you do not recognize.
Check Running Processes and Startup Programs
Monitoring software often runs continuously in the background and may configure itself to launch automatically at startup. Task Manager (Windows) and Activity Monitor (Mac) provide detailed views of active processes and startup items.
Step 1: On Windows, press Ctrl + Shift + Esc or Ctrl + Alt + Del and select Task Manager. On Mac, open Activity Monitor from Applications > Utilities.
Step 2: Review the list of running processes. Look for unfamiliar names, especially those consuming significant CPU, memory, or network resources. Monitoring software may use generic or disguised names, so search online for any process you do not recognize.
Step 3: Check startup programs for unfamiliar entries. On Windows 11, go to Settings > Apps > Startup or use the Startup tab in Task Manager. On Mac, check System Settings > General > Login Items & Extensions.
Disabling or removing unknown startup programs can prevent monitoring tools from launching, but be cautious not to disable essential system processes.
Monitor Network Activity for Suspicious Connections
Many monitoring tools transmit collected data to remote servers. Unusual or unexplained network activity may indicate the presence of such software.
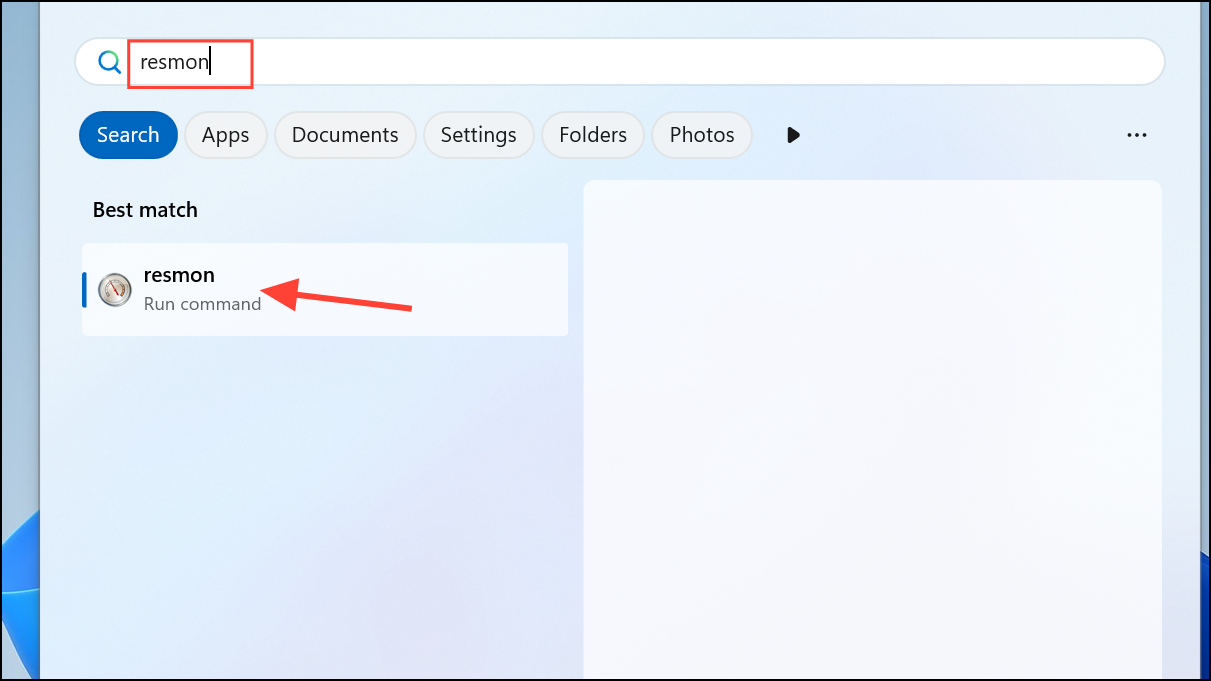
Step 1: On Windows, open Resource Monitor by searching for resmon in the Start menu, then select the Network tab. On Mac, open Activity Monitor and select the Network tab.
Step 2: Examine the list of processes with active network connections. Look for unfamiliar programs consistently sending or receiving data, especially when you are not actively using the internet.
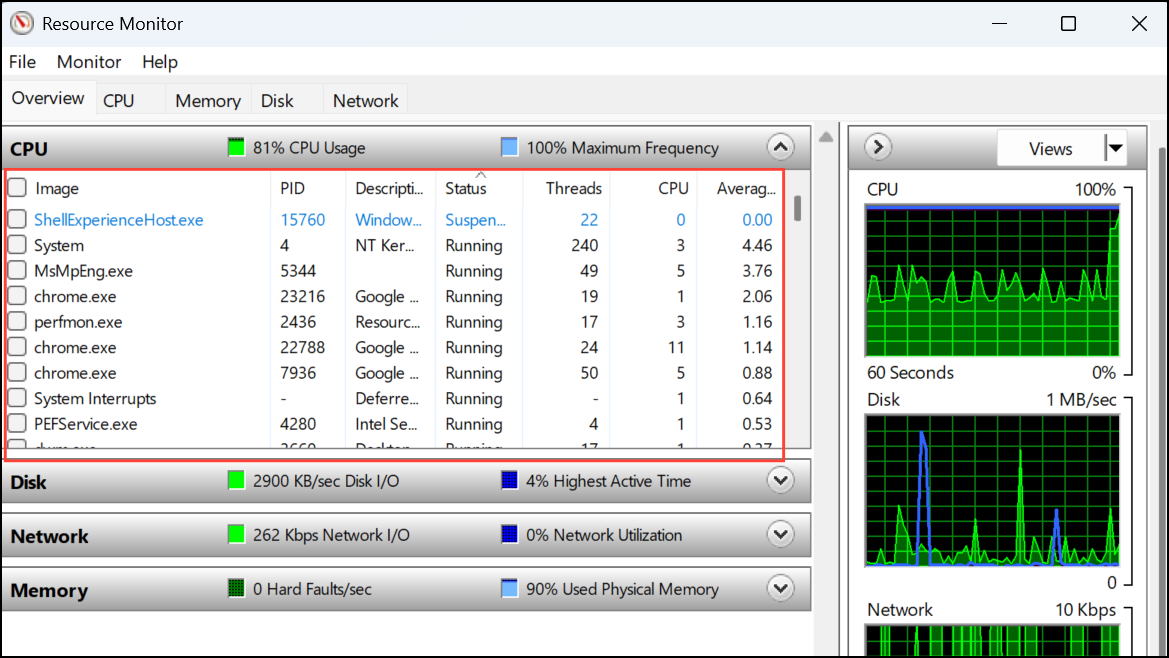
Step 3: Note any unknown IP addresses or domains. Use a reverse IP lookup or online search to identify their origins. Persistent connections to unknown servers may indicate monitoring software in operation.
Third-party tools like GlassWire (Windows) or LuLu (Mac) can provide additional insight into network activity and help you block suspicious traffic.
Inspect Installed Programs and Applications
Monitoring software may appear in your list of installed applications, sometimes under generic or misleading names. Regularly reviewing installed programs can help you spot unauthorized software.
Step 1: On Windows, go to Settings > Apps > Installed Apps or Control Panel > Programs and Features. On Mac, open the Applications folder or check System Settings > General > Storage > Applications.
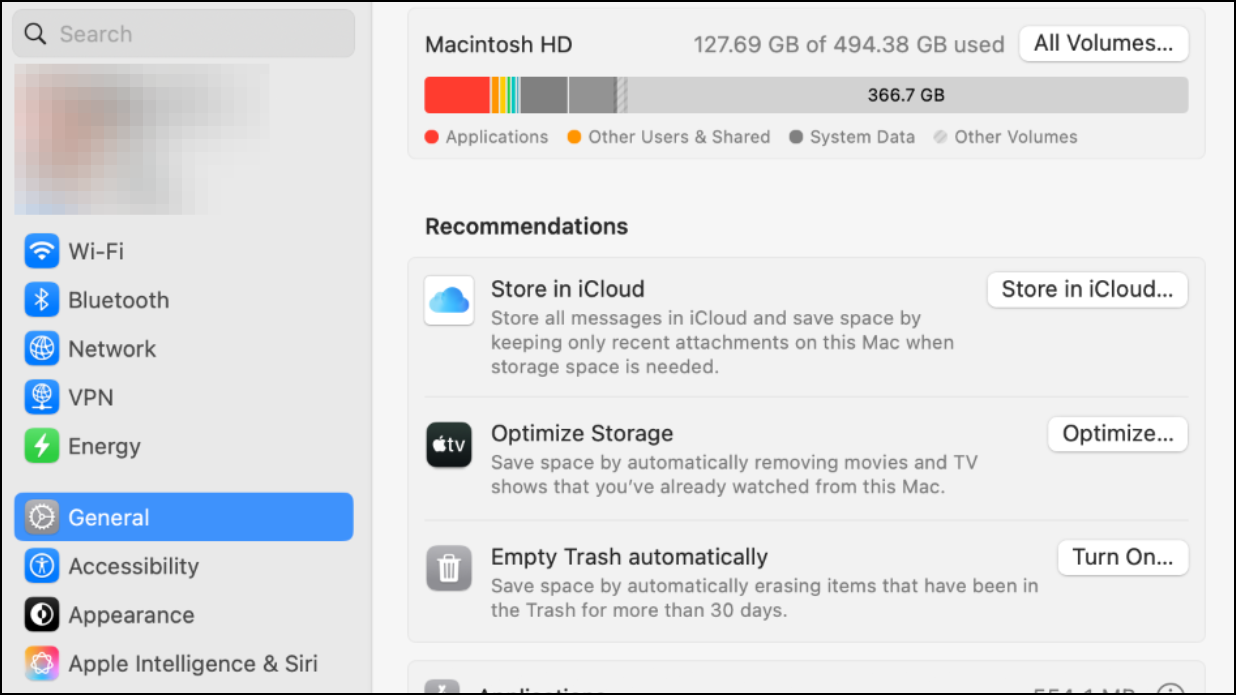
Step 2: Scroll through the list and investigate any applications you do not recall installing. Search online for the software name, developer, and function to determine if it is legitimate or potentially monitoring-related.
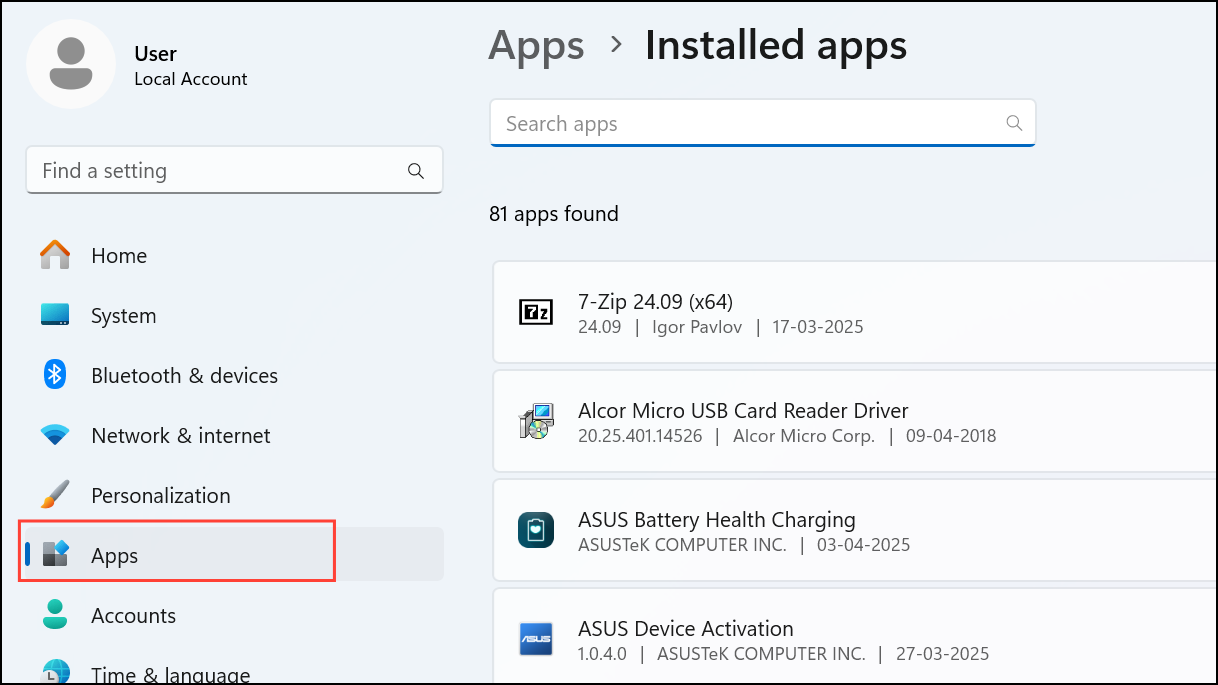
Step 3: If you find suspicious software, attempt to uninstall it. Note that some monitoring programs may restrict uninstallation or require administrator privileges, especially on work or school devices.
Review Browser Extensions and Add-ons
Browser extensions can serve as monitoring tools, tracking web activity, logging keystrokes, or redirecting traffic. Malicious or unauthorized extensions may compromise your privacy.
Step 1: Open your browser’s extensions or add-ons manager (e.g., chrome://extensions for Chrome, about:addons for Firefox).
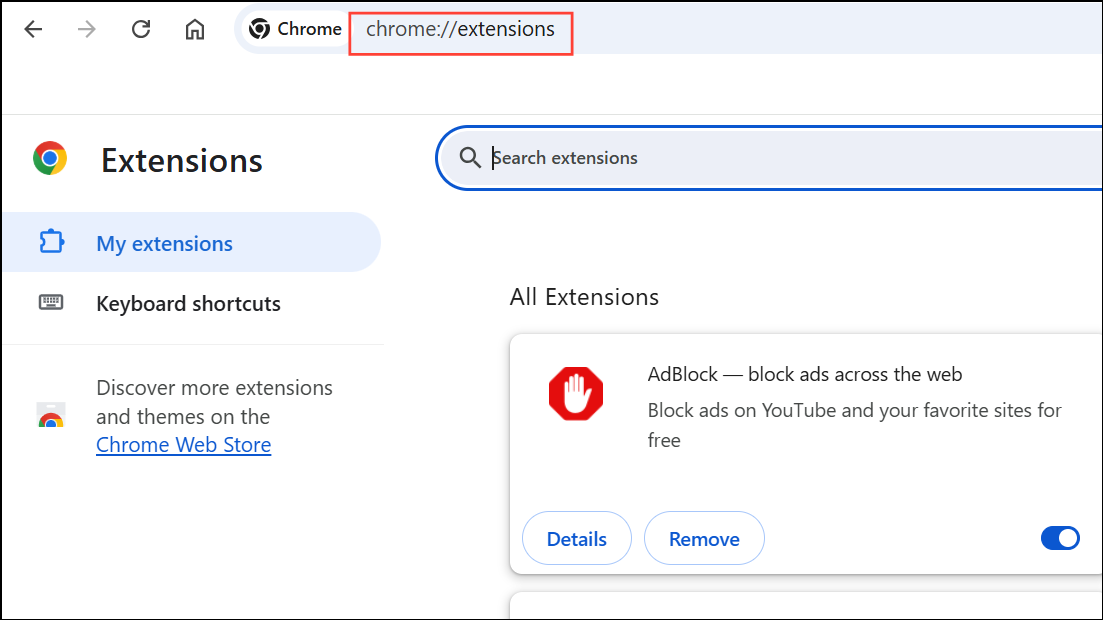
Step 2: Carefully review all installed extensions. Remove any you do not recognize or no longer use, especially those claiming to offer security or productivity features.
Step 3: Research extensions with generic names or few reviews, as these may be disguised monitoring tools. Stick to trusted extensions from reputable developers in the future.
Check Webcam and Microphone Access
Unauthorized access to your webcam or microphone is a serious privacy concern. Monitoring software may activate these devices without your knowledge.
Step 1: On Windows, go to Settings > Privacy & Security > App Permissions and select Camera or Microphone. On Mac, navigate to System Settings > Privacy & Security > Camera/Microphone.
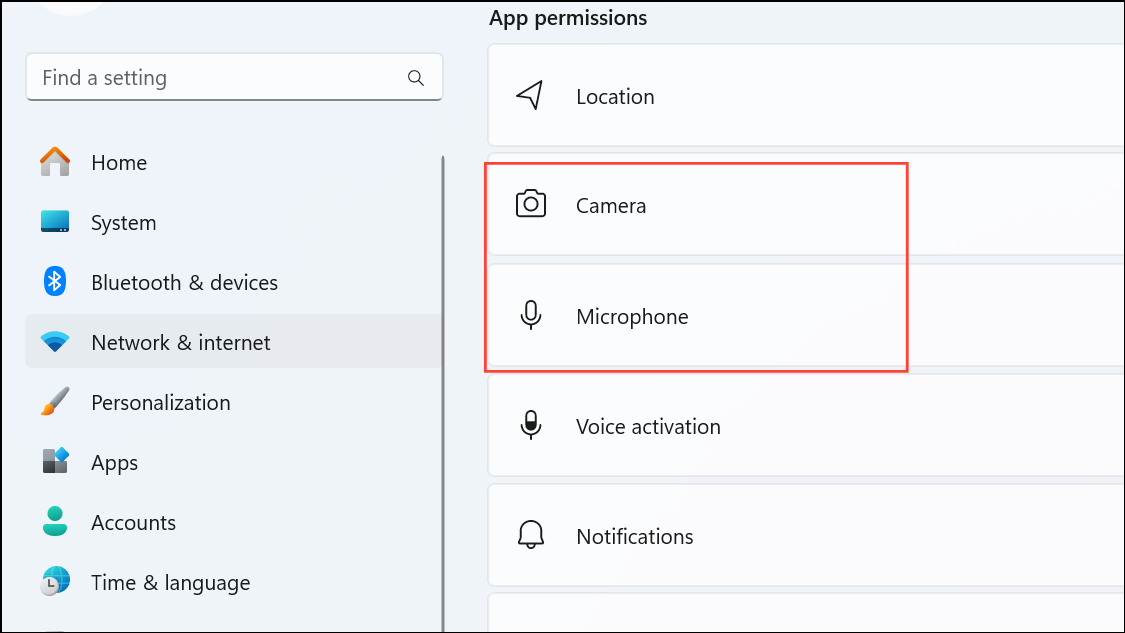
Step 2: Review the list of applications with access. Disable permissions for any app you do not recognize or trust.
Step 3: If your webcam’s indicator light turns on unexpectedly or when no video app is open, investigate immediately. Some advanced monitoring tools can disable the indicator light, so periodic permission reviews are important.
Audit System Logs and Event Viewers for Remote Access
System logs can reveal unauthorized logins or remote access sessions, which may be tied to monitoring activities.
Step 1: On Windows, open Event Viewer via Windows Administrative Tools and navigate to Windows Logs > Security. Look for logon/logoff events outside your normal usage times or from unfamiliar accounts.
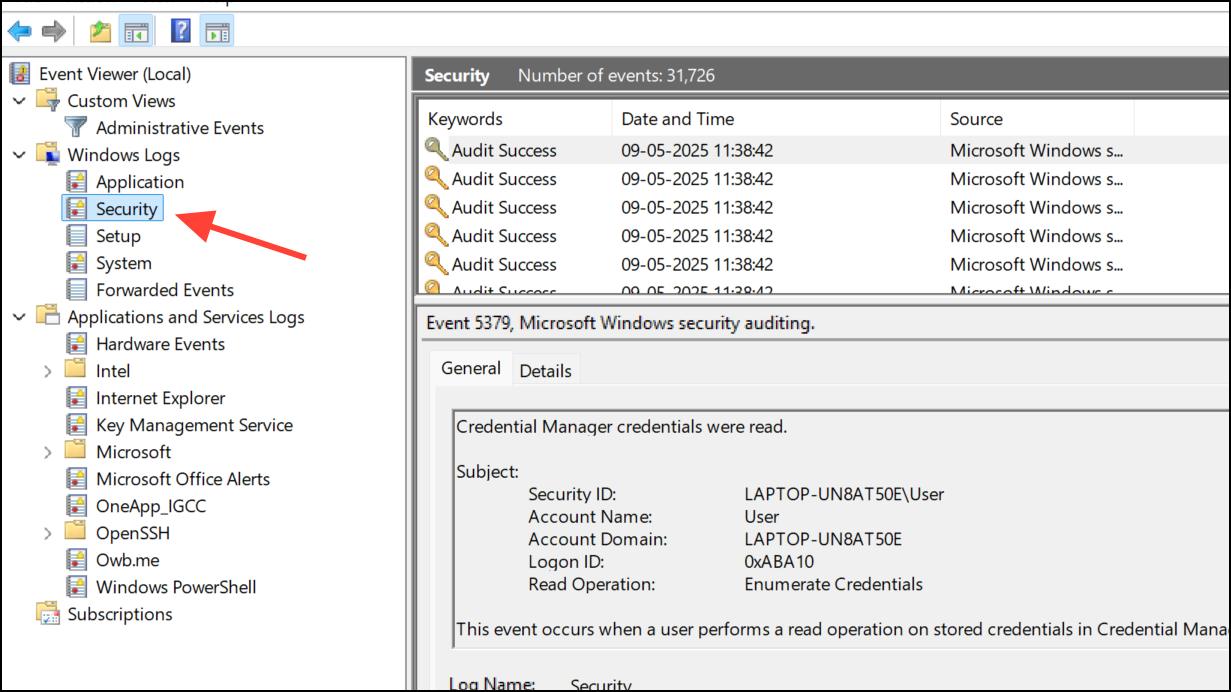
Step 2: On Mac, use the Console app to review system logs for unusual login or remote access activity.
Boot into Safe Mode to Inspect Startup Programs
Some monitoring software hides itself during normal operation but may be visible in Safe Mode, where fewer programs run automatically.
Step 1: Restart your computer and boot into Safe Mode. On Windows, press F8 during startup or use Settings > System > Recovery > Advanced Startup. On Mac, hold Shift during boot.
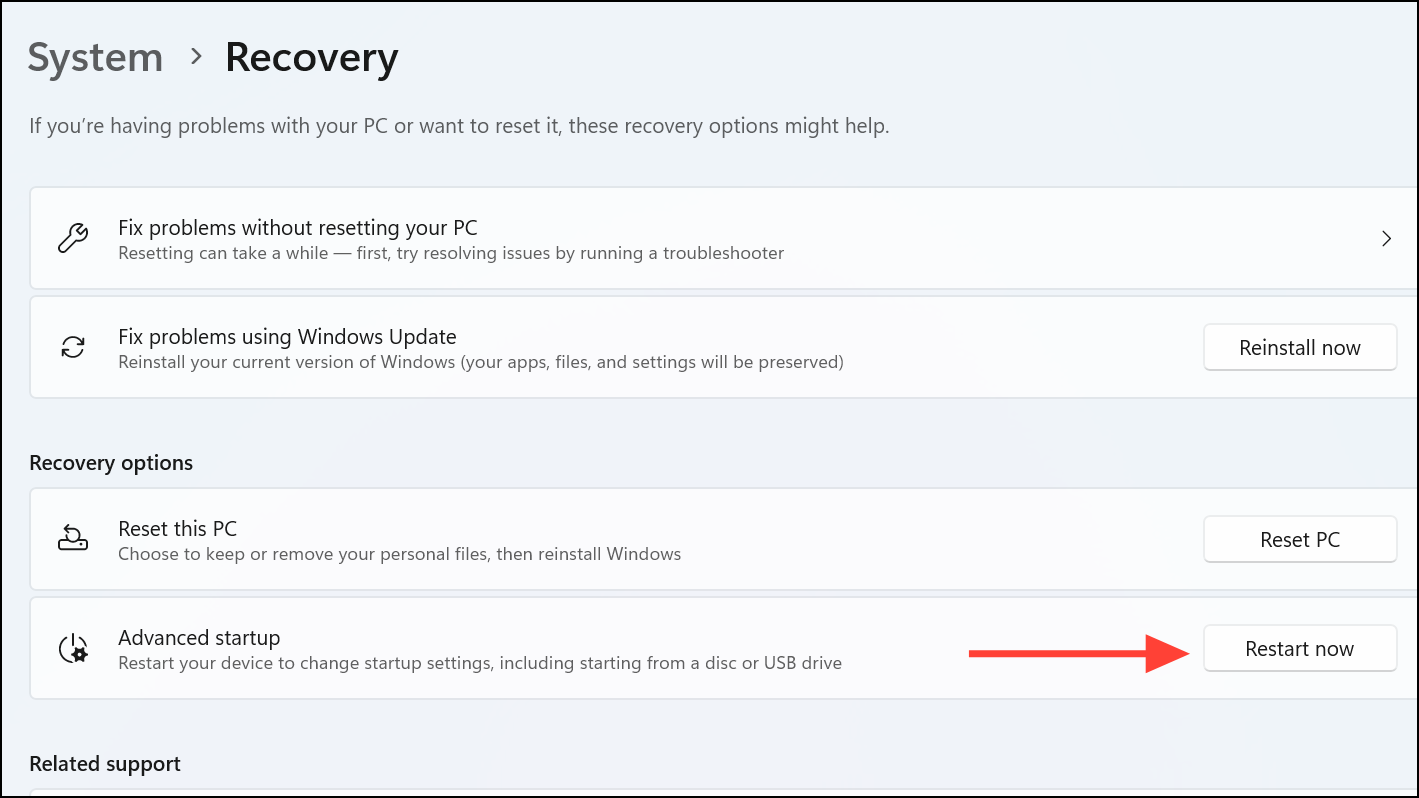
Step 2: Once in Safe Mode, check startup programs via msconfig (Windows) or Login Items (Mac). Unfamiliar entries may indicate hidden monitoring software that fails to conceal itself in this mode.
Regularly reviewing these areas and staying vigilant about unfamiliar software or behavior helps protect your PC from unauthorized monitoring. If you remain concerned after following these steps, consider consulting a security professional or, as a last resort, reinstalling your operating system for a guaranteed clean slate.

