Computers are integral to our daily lives, and protecting them from unauthorized access is crucial. Being hacked can lead to stolen personal data, financial loss, and compromised privacy. Recognizing the signs that your Windows 11 computer has been hacked is essential for taking swift action to secure your system.
1. Check for suspicious connections
One of the most effective ways to determine if your computer has been compromised is by checking for unauthorized network connections. Malware often communicates with remote servers or hackers to transmit data or receive commands. By examining active connections on your Windows 11 system, you can identify suspicious activity.
Look for suspicious connections
Your computer might be maintaining hidden network connections that can be used by hackers to control your system or steal data. You can use the Command Prompt to uncover these hidden connections.
Step 1: Open the Command Prompt with administrative privileges. To do this, search for "Command Prompt" in the Start menu, right-click it, and select Run as administrator.
Step 2: In the Command Prompt window, type the following command and press Enter:
netstat -ano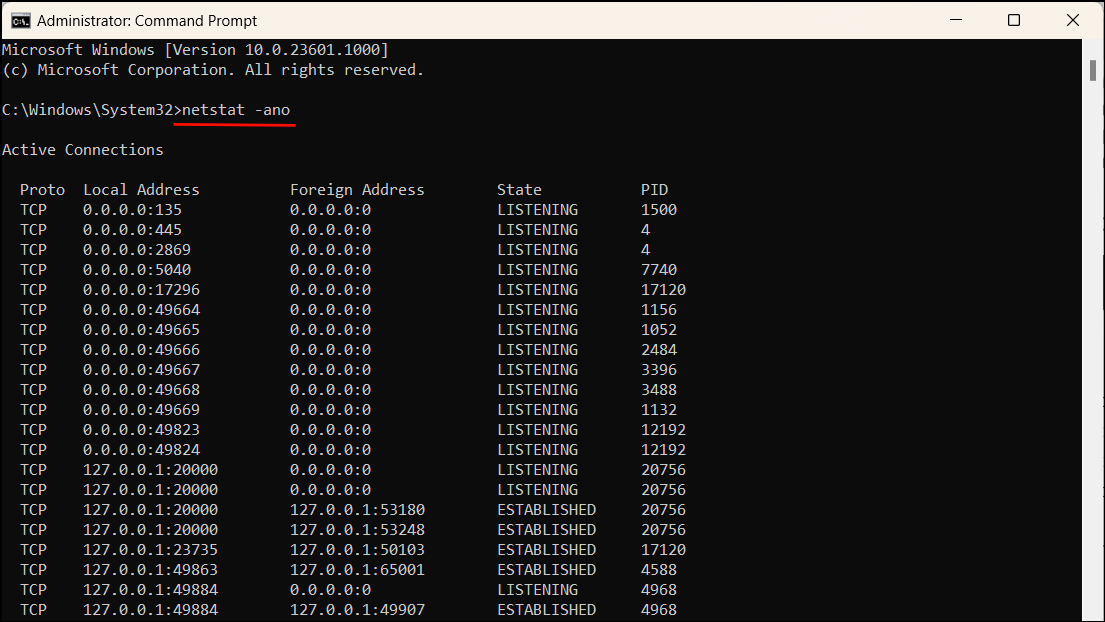
This command lists all active TCP connections. Pay attention to the 'State' column and look for connections that are 'Established'. These indicate ongoing connections between your computer and external IP addresses.
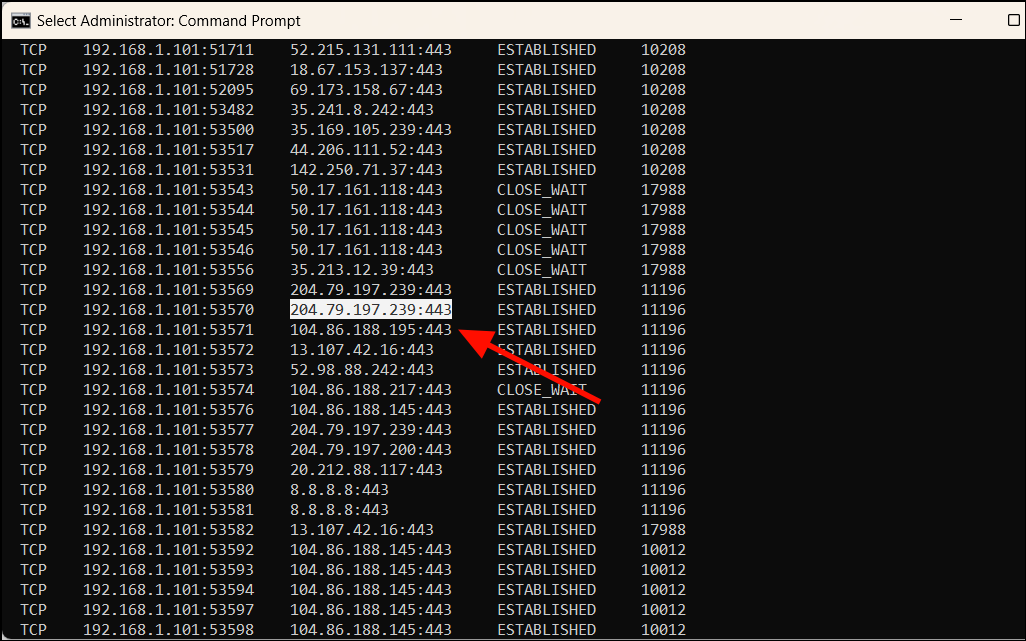
Analyze established connections
Step 3: Identify any Established connections that seem unfamiliar or suspicious. Note the IP addresses listed in the 'Foreign Address' column.
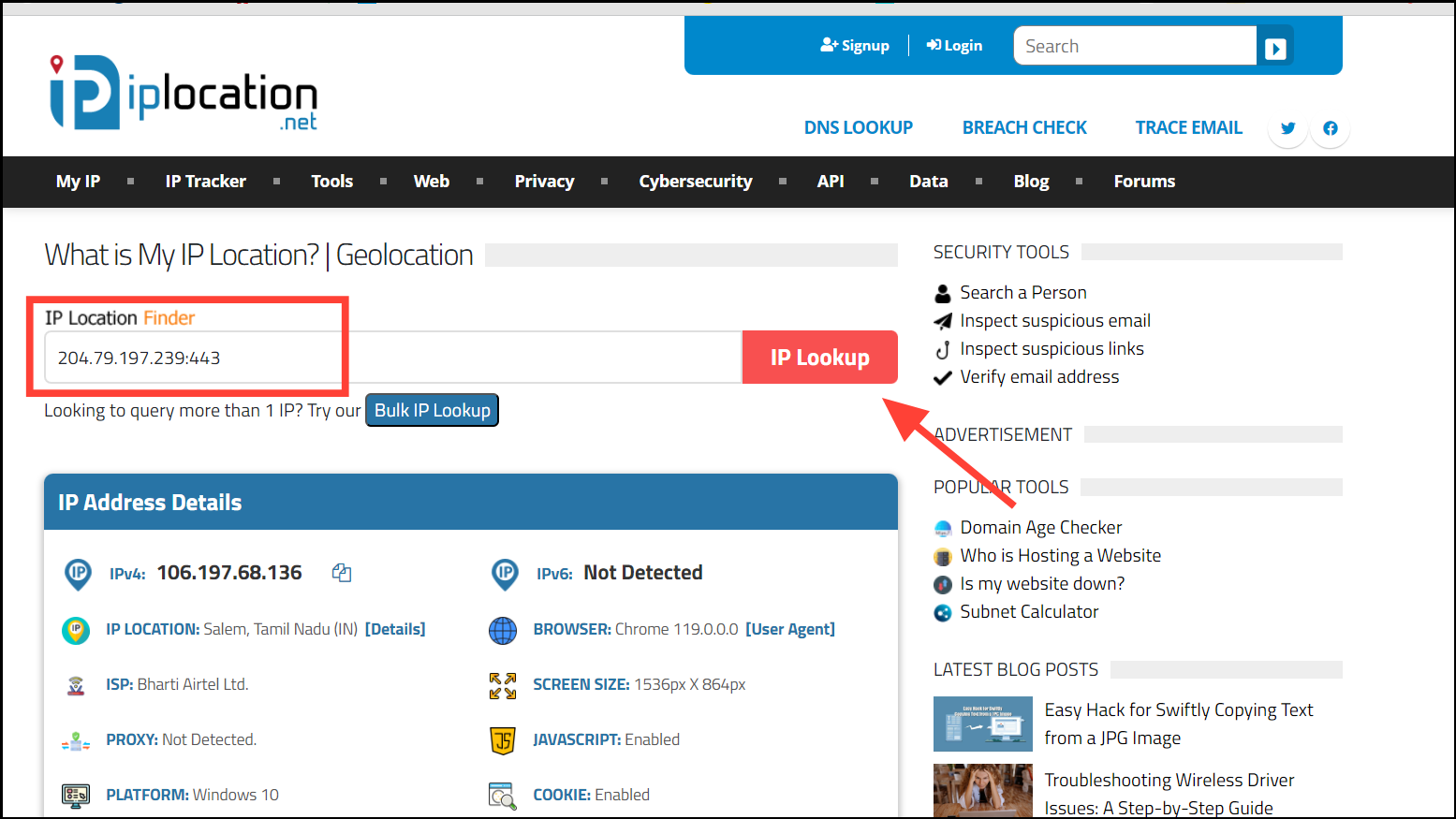
Step 4: To find out more about a specific IP address, copy it and visit an IP lookup service like IPLocation.net. Paste the IP address into the search field and click 'IP Lookup'.
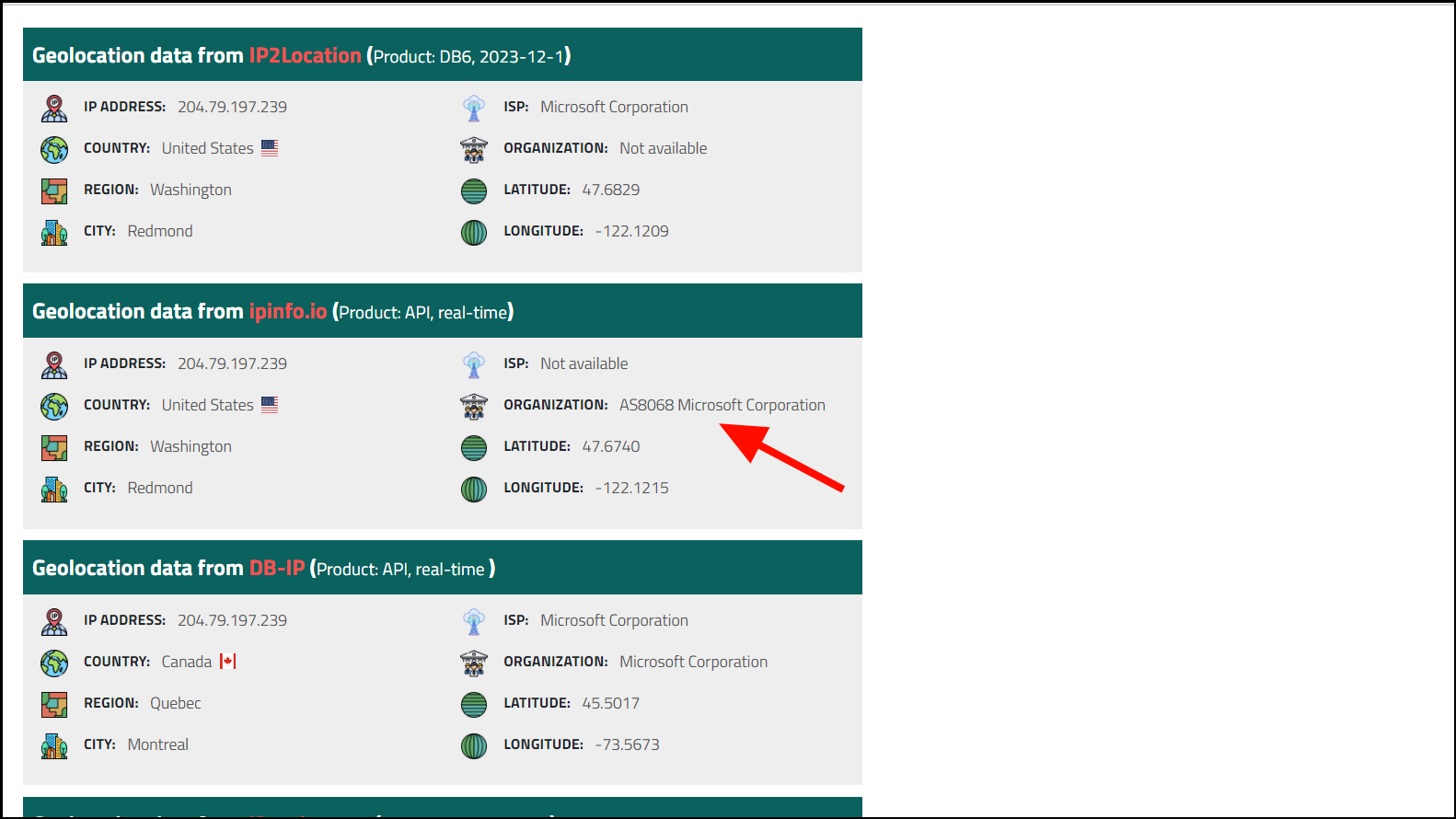
Step 5: Review the details of the IP address, such as the ISP and organization. If it belongs to a known and trusted company like Microsoft or Google, it's likely safe. If the IP address is associated with an unfamiliar or suspicious organization, further investigation is warranted.
By examining active connections, you can detect and address unauthorized access to your computer.
2. Malicious processes in the Task Manager
Another way to detect if your computer has been hacked is by checking for suspicious processes running in the background. Malicious software often disguises itself as legitimate processes, consuming resources and compromising your system. You can use the Task Manager to identify and terminate these processes.
Step 1: Open the Task Manager by right-clicking on the taskbar and selecting Task Manager.
Step 2: Go to the 'Details' tab to see all running processes. Look for any processes with unusual names or those consuming high amounts of CPU, memory, disk space, or network resources.
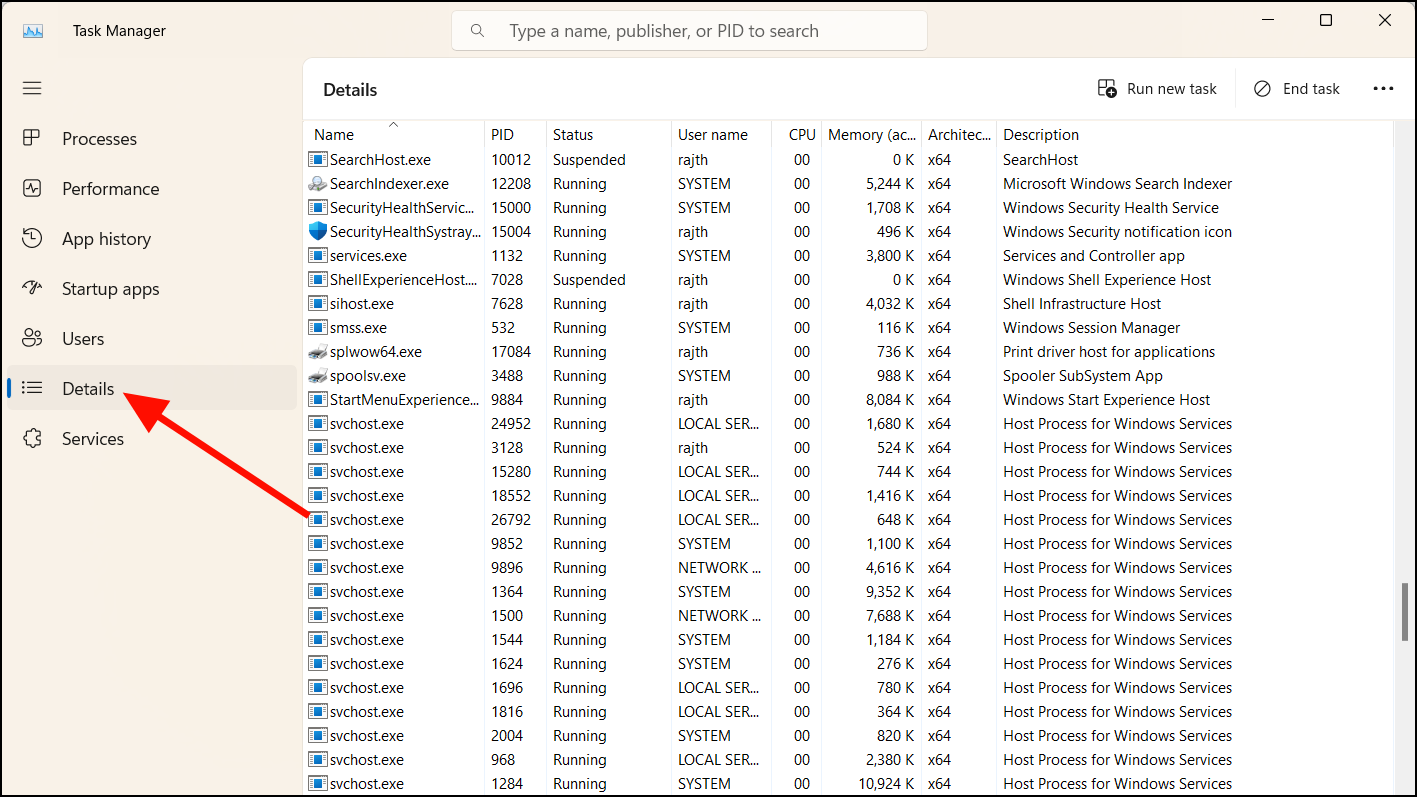
Step 3: Right-click on any suspicious process and select Properties to view more details. Legitimate processes usually have clear descriptions and are associated with trusted publishers.
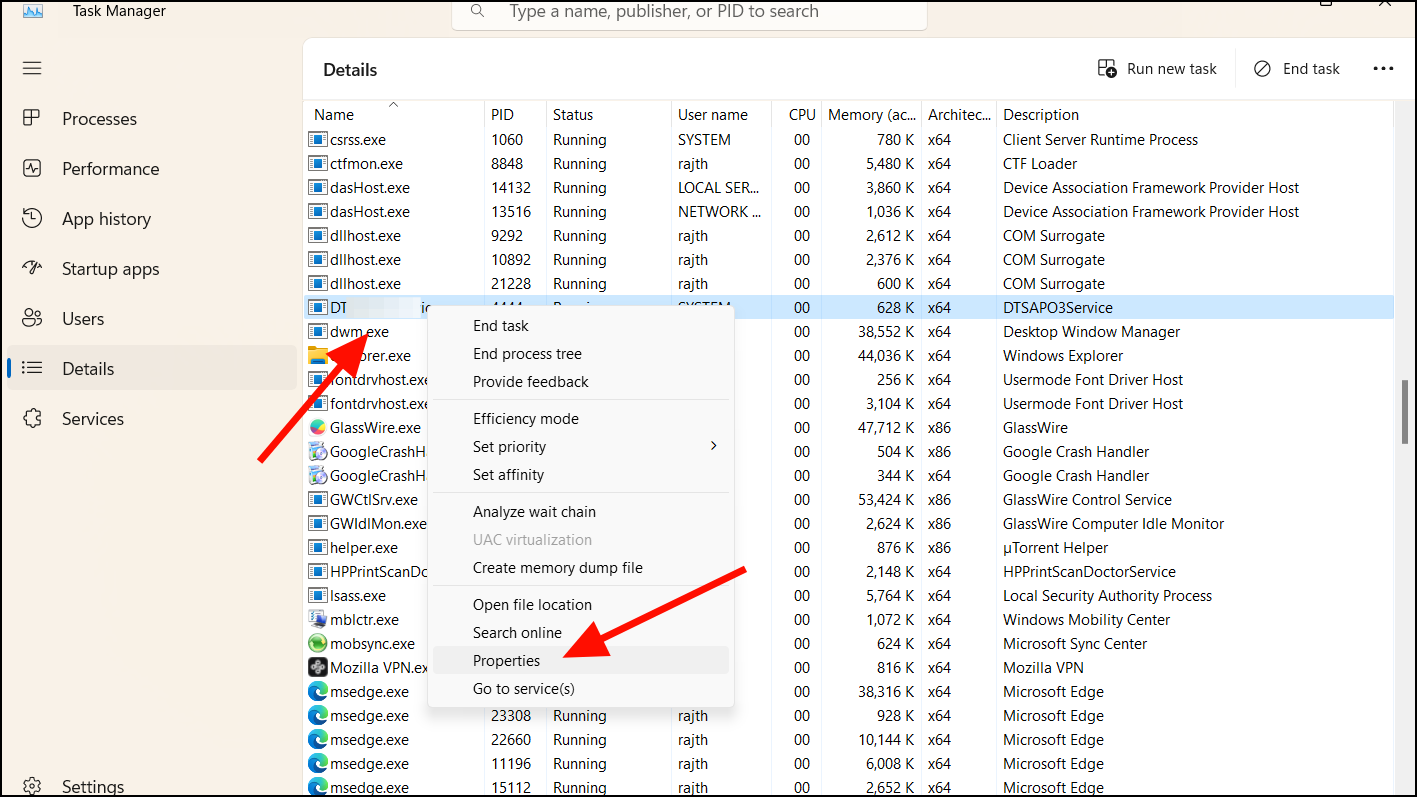
Step 4: In the properties window, check the 'Details' tab for information like the file description and copyright. If these fields are blank or seem suspicious, the process might be malicious.
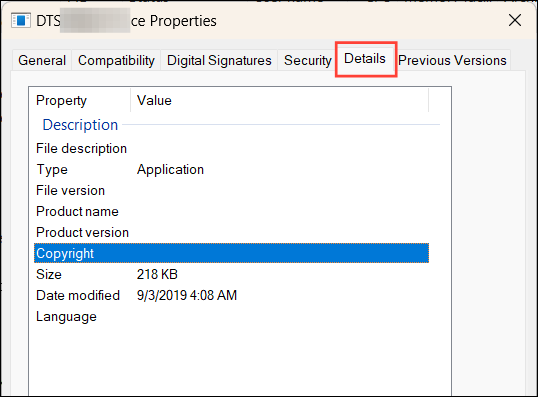
By carefully examining running processes, you can spot and eliminate malware that may be compromising your system.
3. Suspicious software on your PC
Unexpected software appearing on your computer is a major red flag. Hackers often install malicious programs without your knowledge to steal data, monitor your activities, or control your system. Regularly reviewing installed applications can help you detect unauthorized software.
Check for unfamiliar programs in your Start menu, desktop, or system tray. Some malware may not display visible icons but can still run in the background. Open the Task Manager and look for processes with unusual names or high resource usage.
Research any unknown software by searching online for reviews or warnings. If you confirm that the software is malicious, remove it immediately using your antivirus program or by uninstalling it through the Control Panel.
4. Disabled security tools
If your antivirus or security software is unexpectedly disabled or not functioning properly, it could indicate that your computer has been compromised. Malware often attempts to disable security programs to avoid detection.
Ensure that your antivirus software is up to date and running scans regularly. If you're unable to open or update your security tools, try reinstalling them. If the problem persists, your system may be infected with malware that requires specialized removal tools.
5. Your passwords or logins stopped working
Discovering that your passwords no longer work is a serious indication of a security breach. Hackers may change your account credentials to lock you out and gain full control.
If you cannot access your accounts, act quickly:
- Attempt to reset your passwords using the "Forgot Password" feature.
- Enable two-factor authentication (2FA) if available.
- Contact the service provider to report unauthorized access.
Regularly updating your passwords and using unique passwords for each account can help prevent unauthorized access.
6. Suspicious logins
Monitoring your account activity can reveal unauthorized access. Many online services provide logs of recent login attempts, including the time, location, and device used.
Review your account settings for any unfamiliar activity:
- Check recent login history for unknown locations or devices.
- Look for unrecognized connected devices or active sessions.
- Review account settings for changes you didn't make.
If you notice any suspicious activity, secure your account by changing your password and enabling 2FA.
7. Your web browser is modified
Unexpected changes to your web browser can indicate malware infection. Signs include a changed homepage or search engine, new toolbars or extensions you didn't install, and increased pop-up ads or redirects.
- Unknown extensions or toolbars: Check your browser's extensions and remove any you didn't install.
- Homepage or search engine changes: Reset your browser settings to restore your preferred homepage and search engine.
- Pop-up ads and redirects: Use a reputable malware scanner to remove adware causing unwanted ads.
Keeping your browser up to date and only installing trusted extensions can help prevent these issues.
8. Unusual network activity
Unexplained spikes in network activity, especially when you're not using the internet, can be a sign of unauthorized access. Malware or hackers may be using your bandwidth to transmit data or conduct attacks.
You can monitor network activity using tools like GlassWire or Nagios Core. These programs display which applications are using your network resources, helping you identify and stop suspicious activity.
9. Peripherals are acting strangely
Unusual behavior from peripherals like your mouse, keyboard, webcam, or microphone can indicate that someone has gained remote access to your computer.
- The cursor moves or clicks on its own.
- The webcam or microphone activates without your input.
- Files are copied or moved without your action.
- Printers or other devices behave erratically.
While hardware issues can sometimes cause similar symptoms, it's important to rule out malware by scanning your system with updated security software.
10. Rapid battery drain and noisy fans
If your computer's battery is depleting quickly and the fans are running loudly, it could be due to malware consuming system resources.
Signs include:
- Fans running at high speeds when the system is idle.
- The device feeling unusually warm.
- Battery life significantly reduced.
Use the Task Manager to identify processes using excessive resources and terminate any suspicious ones.
11. Your network traffic and searches are redirected
Hackers may alter your DNS settings to redirect your internet traffic to malicious sites. Signs of this include:
- Search results leading to irrelevant or spammy websites.
- Increased pop-ups and ads from unknown sources.
- Your browser's homepage changing without your consent.
Reset your router and computer's DNS settings to the default values or use trusted DNS services. Scanning for malware can also help remove any software causing these redirects.
12. Your PC performance is low and apps crash
System slowdowns and frequent application crashes can be symptoms of malware. Malicious software can consume a lot of resources, leaving legitimate applications struggling to operate.
Indicators include:
- Slow loading times for websites and apps.
- Media playback freezing or stuttering.
- Apps crashing unexpectedly.
Use the Task Manager to monitor resource usage and identify any suspicious processes. Running a full system scan with your antivirus software can help detect and remove malware.
13. You receive a ransom message
One of the most blatant signs of a hacked computer is receiving a ransom message. Ransomware can lock you out of your system or encrypt your files, demanding payment for access.
If you encounter a ransom message:
- Do not pay the ransom; there's no guarantee you'll regain access.
- Try to boot your system in Safe Mode and run a malware removal tool.
- If necessary, restore your system from a backup or reinstall the operating system.
14. Verifying if your personal data has been compromised in a data breach
Data breaches can expose your personal information without your knowledge. Websites like Have I Been Pwned allow you to check if your email address has been involved in a known breach.
Visit the website, enter your email address, and click the 'pwned?' button to see if your data has been compromised. If your information has been exposed, change your passwords immediately and consider enabling 2FA.
How to prevent your PC from being hacked
While no system is entirely immune to attacks, following best practices can significantly enhance your computer's security:
- Install reputable antivirus and anti-malware software.
- Avoid downloading pirated software and games.
- Be cautious with emails from unknown senders and avoid clicking on suspicious links.
- Use strong, unique passwords for each of your accounts.
- Be wary of using unfamiliar USB drives, as they may contain malware.
- Enable and properly configure your firewall to block unauthorized access.
- Only download software from trusted sources.
- Avoid conducting sensitive activities over public Wi-Fi networks.
- Regularly back up important files to protect against data loss.
- Enable two-factor authentication on your accounts whenever possible.
- Keep your Windows operating system and all software up to date with the latest security patches.
If you suspect that your computer has been hacked, it's crucial to act promptly. The sooner you address the issue, the less damage potential attackers can cause.
Staying vigilant and proactive about your computer's security can help protect your data and privacy from malicious attacks.

